Search by Tag
Lag-and-Crash-2.0
25 March 2022Escape From Gulag
### Upon connecting to the server, I can see that I have to select a shell. However, most of the...
pwnLag-and-Crash-2.0
25 March 2022We Need Flash
### Upon connection, I got the following message from the server. So, there will be a test I have to...
pwnLag-and-Crash-2.0
26 March 2022Lag and Crash 2.0
Web Hacking Fundamentals
16 August 2021Pickle_rick
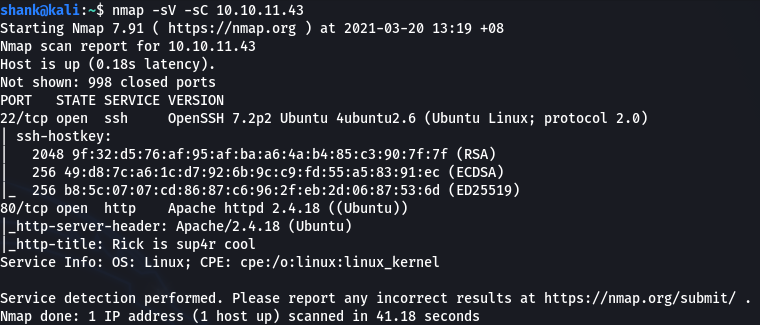
First a nmap scan was conducted to determine the running services on the machine. Turns out it was running apache (web service) and SSH
nmap -sV -sC 10.10.11.43
Web Hacking Fundamentals
16 August 2021Web Hacking Fundamentals
General
17 August 2021Simple_ctf
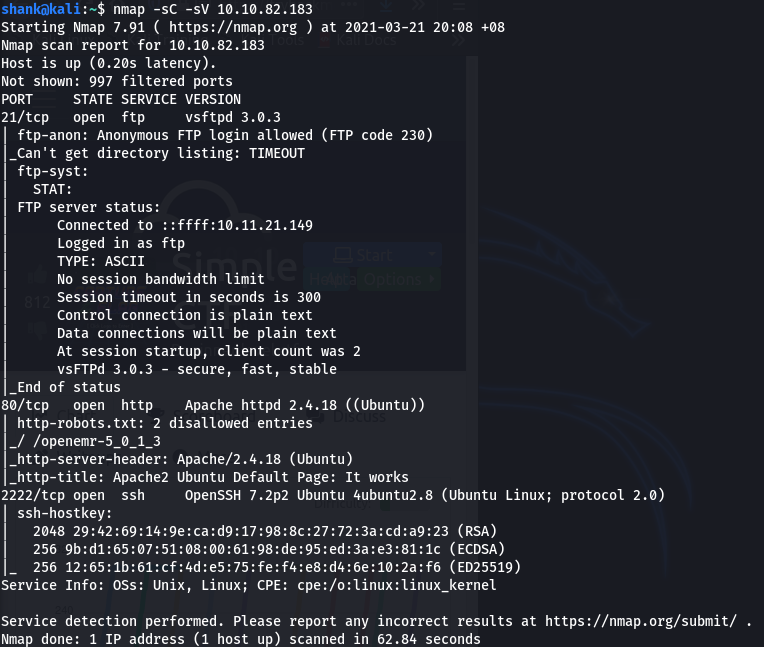
An nmap scan was conducted on the machine and results shown that few services were running which included ftp, apache & ssh
nmap -sV -sC 10.10.82.183
General
19 August 2021Ice
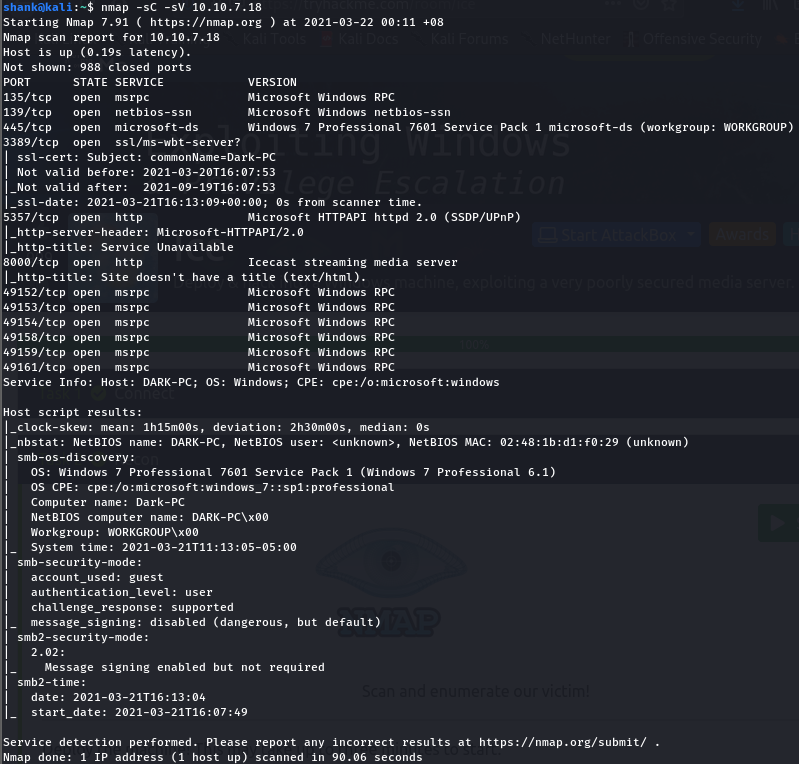
A simple nmap scan was conducted on the machine. Interesting services like rdp, http were running. Something eye catching was found where a service called icecast was running for http
nmap -sV -sC 10.10.7.18
Advanced Exploitation
20 August 2021Steel_mountain
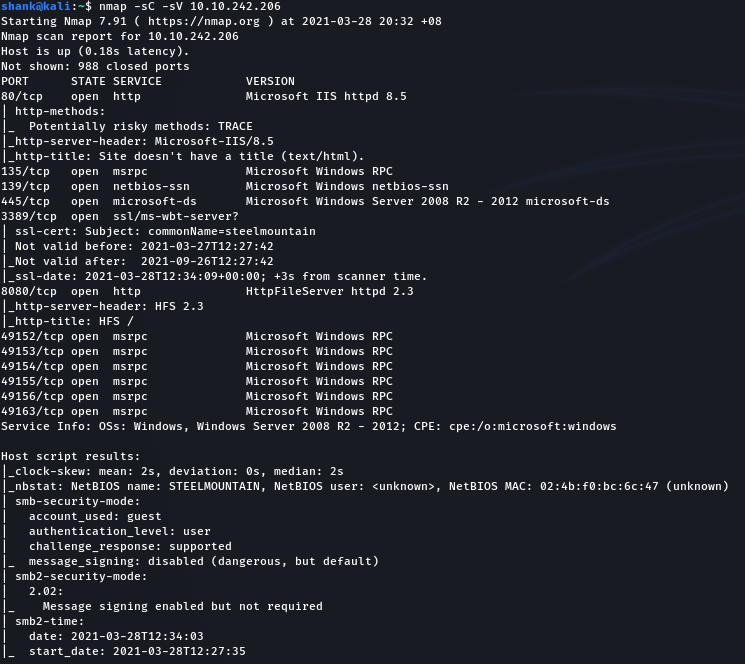
A basic nmap scan was conducted on the machine and results show that web service is running on port 80 & 8080. RDP service is also running
nmap -sV -sC 10.10.242.206
Advanced Exploitation
28 August 2021Alfred
A simple nmap scan was conducted on the machine. Turns out it is running a website on port 80 and 8080. Also running RDP on port 3389
jenkins, windows_tokensGeneral
29 August 2021Rootme
Nmap scan shows that ssh and apache services are running
web, linux, privilege-escalationGeneral
01 December 2021Agent_sudo
Basic nmap scan results show that, the machine is running 3 services: ssh, ftp, http
enumeration, brute-forceGeneral
01 December 2021General
Advanced Exploitation
06 December 2021Hackpark
A simple nmap scan was conducted on the machine. Turns out it is running a website
web, windowsAdvanced Exploitation
06 December 2021Advanced Exploitation
Basic Exploitation
30 January 2022Game_zone
A rust scan was used to conduct a speed scan on the IP and pipe the open ports to conduct a nmap scan. From what it shows, ports 22 and 80 are open
SQLi, RCEBasic Exploitation
30 January 2022Basic Exploitation
Offensive Pentesting
31 January 2022Daily_bugle
Rust Scan scanning tool was used to enumerate the running services on the server. Turns out it has SSH, Web service Joomla and MySQL Database running
SQLi, joomla, RCEOffensive Pentesting
02 February 2022Relevant
Rust Scan scanning tool was used to enumerate the running services on the server. From the ports that look open, it looks like this is a windows machine. This is confirmed with the Nmap results we got
windows, smb, SeImpersonatePrivilegeOffensive Pentesting
02 February 2022Offensive Pentesting